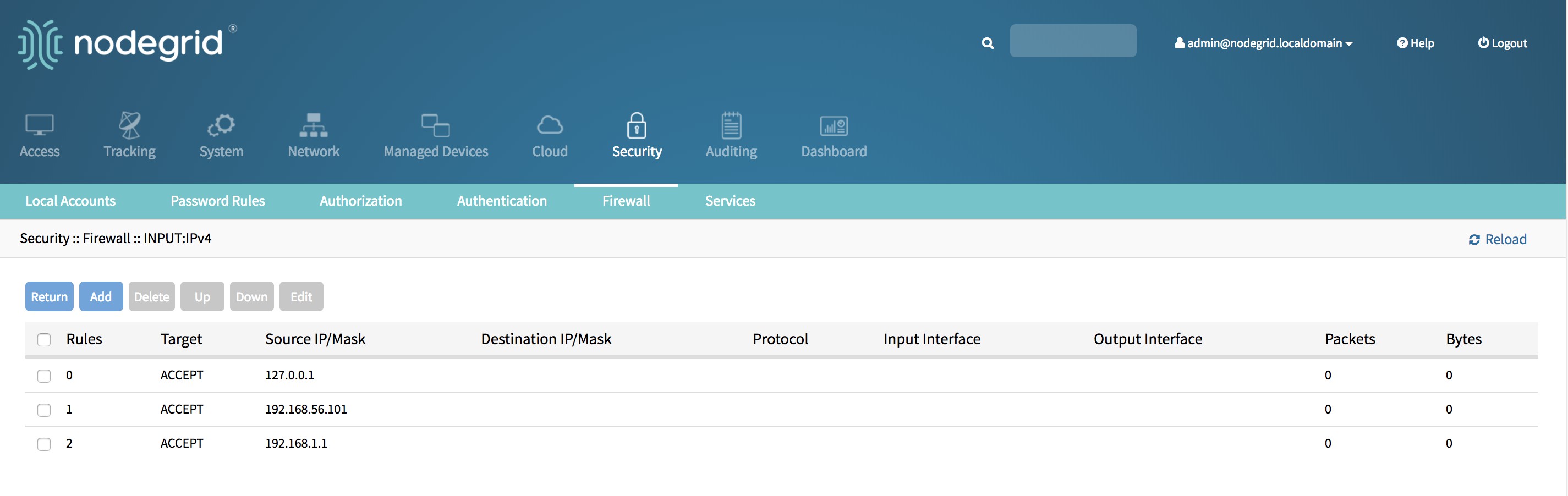
Create a new Rule through CLI
Log in to the Nodegrid device CLI using admin account.
Navigate to the desired firewall chain. By default, the following 6 Chains are available:
IPv4 INPUT
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/INPUT/IPv4 FORWARD
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/FORWARD/IPv4 OUTPUT
[admin@nodegrid /]# cd /settings/ipv4_firewall/chains/OUTPUT/IPv6 INPUT
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/INPUT/IPv6 FORWARD
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/FORWARD/IPv6 OUTPUT
[admin@nodegrid /]# cd /settings/ipv6_firewall/chains/OUTPUT/Type add to create a new rule
[admin@nodegrid INPUT]# addUse the set command to create the new rule settings. Press TAB twice to see all available options
[admin@nodegrid {INPUT}]# set target=ACCEPT source_net4=192.168.1.1Use the save command to create and activate the new rule
[admin@nodegrid {INPUT}]# saveUse the show command to see the current values for the rule:
[admin@nodegrid 2]# show
target = ACCEPT
source_net4 = 192.168.1.1
destination_net4 =
protocol = tcp
source_port =
destination_port = 443
tcp_flag_syn = any
tcp_flag_ack = any
tcp_flag_fin = any
tcp_flag_rst = any
tcp_flag_urg = any
tcp_flag_psh = any
input_interface = any
output_interface = any
fragments = all_packets_and_fragments
reverse_match_for_source_ip|mask = no
reverse_match_for_destination_ip|mask = no
reverse_match_for_source_port = no
reverse_match_for_destination_port = no
reverse_match_for_protocol = no
reverse_match_for_tcp_flags = no
reverse_match_for_icmp_type = no
reverse_match_for_input_interface = no
reverse_match_for_output_interface = no
reject_with = port_unreacheable
log_level = debug
log_prefix =
log_tcp_sequence_numbers = no
log_options_from_the_tcp_packet_header = no
log_options_from_the_ip_packet_header = noA list of currently active IPv4 rules can be see with the command shell sudo /usr/sbin/iptables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/iptables -L -nvx
Chain INPUT (policy ACCEPT 110 packets, 13509 bytes)
pkts bytes target prot opt in out source destination
1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1182 132492 ACCEPT all -- * * 127.0.0.1 0.0.0.0/0
59 32478 ACCEPT all -- * * 192.168.56.101 0.0.0.0/0A list of currently active IPv6 rules can be see with the command shell sudo /usr/sbin/ip6tables -L -nvx
[admin@nodegrid /]# shell sudo /usr/sbin/ip6tables -L -nvx
Chain INPUT (policy DROP 1 packets, 72 bytes)
pkts bytes target prot opt in out source destination
2 132 ACCEPT all lo * ::/0 ::/0
0 0 ACCEPT all * * ::1 ::/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy DROP 8384 packets, 428444 bytes)
pkts bytes target prot opt in out source destination
2 132 ACCEPT all * * ::1 ::/0Create a new Rule through WebUI
Log in to the Nodegrid Manager Web UI with an admin account.
Go to Security::Firewall.
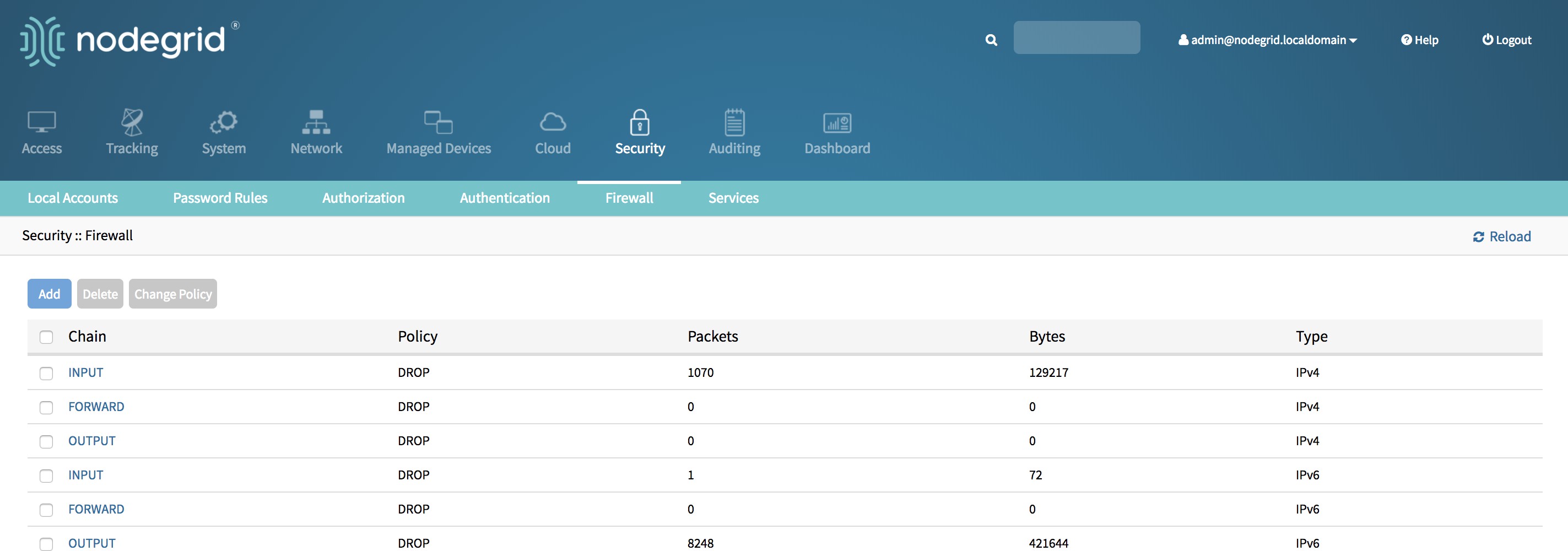
Click on the desired Chain, by default the following 6 chains are available:
- INPUT - Type IPv4
- FORWARD - Type IPv4
- OUTPUT - Type IPv4
- INPUT - Type IPv6
- FORWARD - Type IPv6
- OUTPUT - Type IPv6
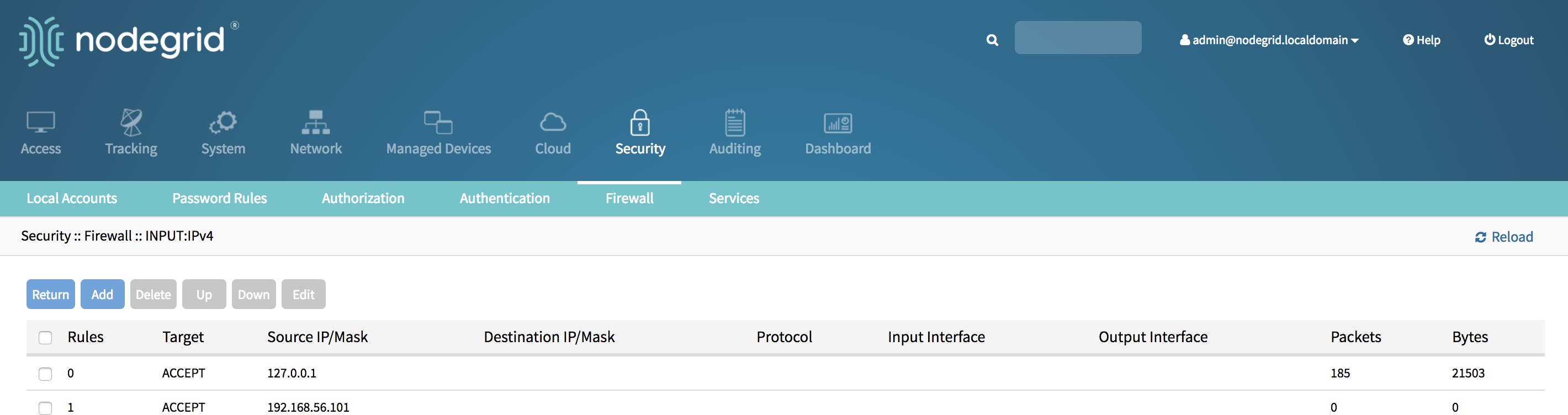
Click Add to create a new rule.
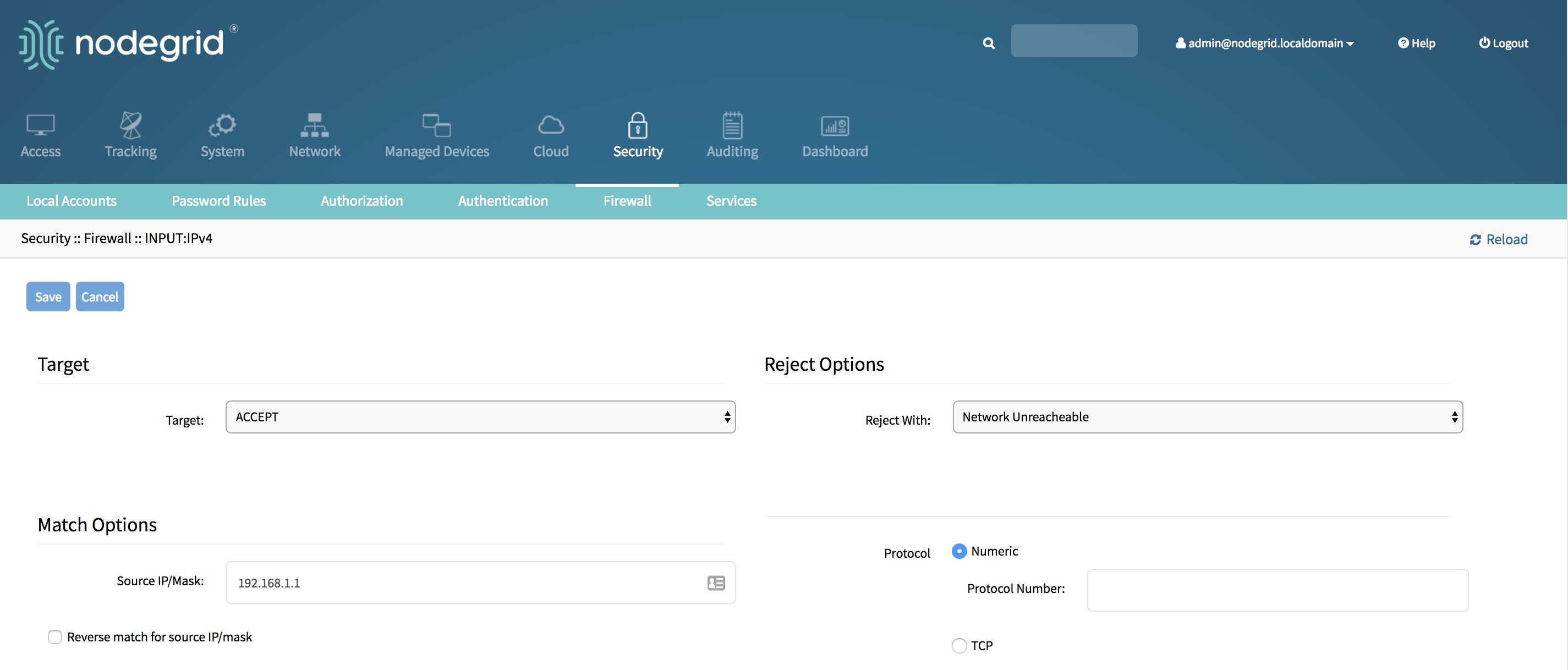
Enter the desired values for the new rule and click Save. The new rule will saved and will be effective immediately