General security service settings are configured on this page. It is recommended to prepare a document that defines how the company security requirements are implemented with the device security settings. To configure general services:
Log in the Nodegrid Web UI.
Go to Security :: Services :: General Services.
Configure the settings as described in the following sections.
ZPE Cloud section(cloud-based management platform for Nodegrid products):
Setting | Description | Default |
Enable ZPE Cloud | Select Enable ZPE Cloud checkbox (Nodegrid NSR, GSR, BSR, LSR, HSR - default: enabled. Nodegrid Serial Console - default: disabled). When Once enabled you can access this device from the ZPE cloud. | Nodegrid NSR, GSR, BSR, LSR, HSR: Enabled |
ZPE Cloud URL | This is a read-only field, that automatically populates the URL to the ZPE cloud. | N/A |
Enable Remote Access | Check this field to remotely access the device, this is useful when you want to take the backup of the data. | Nodegrid NSR, GSR, BSR, LSR, HSR: Enabled |
Enable File Protection (Optional) | If enabled, file transfer requires an authentication hash based on this password to validate file integrity and origin. The field is disabled by default. If enabled, enter Passcode and Confirm Passcode. | Disabled |
Enable File Encryption | On the File Encryption Mode menu (select one):
| Disabled |
Active Services
Setting | Description | Default |
System Profile | The default profile is populated in the System Profile. | Out of Band |
Enable detection of USB devices | Detects if any USB is attached to the device. | Enabled |
Enable RPC | Enable if you want to request services from other programs on a different machine in a network. | Disabled |
Enable gRPC | Enables gRPC service. Specify the gRPC Port (default: 4830). | Disabled |
Enable FTP Service | Enables FTP service for file transfers. | Disabled |
Enable SNMP Service | Enables SNMP for network management. | Enabled |
Enable Telnet Service to Nodegrid | Allows Telnet access to Nodegrid. Specify the Telnet TCP Port (default: 23). | Disabled |
Enable Telnet Service to Managed Devices | Allows Telnet access to managed devices. | Disabled |
Enable ICMP echo reply | Enables ICMP echo reply for network diagnostics. | Enabled |
Enable ICMP secure redirects | Enables secure redirects for ICMP. | Enabled |
Enable USB over IP | Enables USB over IP protocol. | Disabled |
Enable Search Engine | Enables the device’s search engine. Optionally, enable Dashboards. | Enabled |
Enable Telegraf | Enables Telegraf service for data collection. | Disabled |
Enable Services Status Page | Provides a status page at `<NG URL>/services/status` to determine functioning services. | Enabled |
Enable reboot on Services Status Page | Allows device reboot via the services status page. | Enabled |
Enable keepalived | Maintains a keepalive session for the Nodegrid device, ensuring it starts during system reboot. You can also enable the keepalived setting via the CLI by entering the following command: | Disabled |
Virtualization Services
Setting | Description | Default |
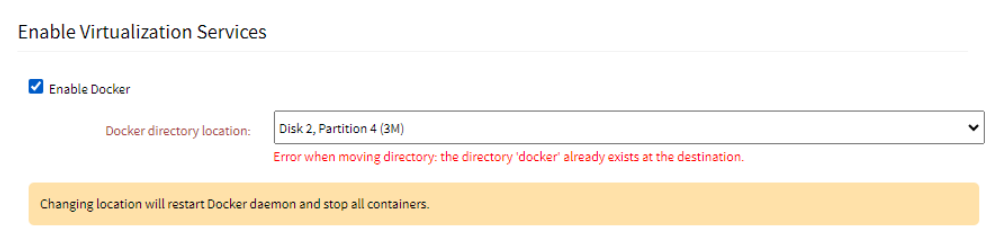
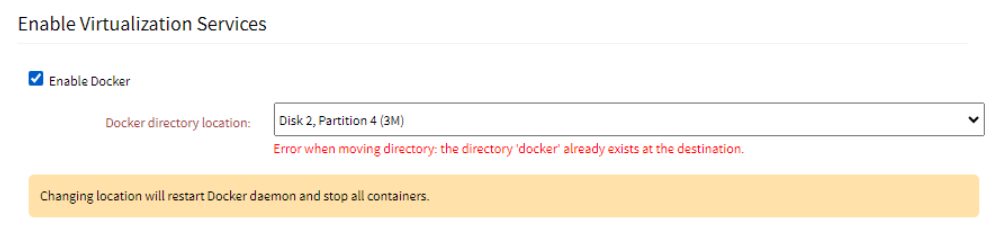
Enable Docker | When you enable the field, the Docker directory location drop-down list is displayed. It lists all the suitable locations to which the Docker daemon and its files can be moved and lists any disk or partition that is formatted and mounted. The Default option points to the primary disk location; /var/lib. If there is not enough space in the selected folder, an error is displayed:
If there is an existing folder called Docker, an error is displayed:
| Enabled |
Enable Qemu/KVM | Enables Qemu/KVM virtualization. | Enabled |
Enable VMware Manager | Enables VMware Manager for virtualization management. | Enabled |
Cluster TCP Port | Specify the Cluster TCP Port (default: 9966). | 9966 |
Enable Automatic Cluster Enrollment | Enables automatic enrollment for clusters. | Disabled |
Search Engine TCP Port | Specify the Search Engine TCP Port (default: 9300). | 9300 |
Enable VM Serial access | Enables serial port for virtual machine access. | |
|
|
|
Enable Zero Touch Provisioning | Enables ZTP for the device. | Enabled |
Enable Bluetooth | Enables Bluetooth access to the Nodegrid device.
| Disabled |
|
| <ProductName_SerialNumber> |
Disabled | ||
Enable PXE (Preboot eXecution Environment) | Enables boot a software image retrieved at boot time from a network server. | Enabled |
Block Host with multiple authentication failures | Blocks hosts when authentication fails multiple times.
| Disabled |
Allow root console access | Provides administrators the ability to control access to the primary console interface, which includes both the Console Serial Port and the Video VGA/HDMI and USB Keyboard ports.
| Enabled |
Manage devices
Setting | Description | Default |
Device access is enforced via user group authorization | Enables users to only access devices listed in the user's authorization groups. If not enabled, all enrolled devices are available). | Disabled |
Enable the Autodiscovery | Enables autodiscovery of the devices when connected to the network. | Enabled |
FIPS
Setting | Description | Default |
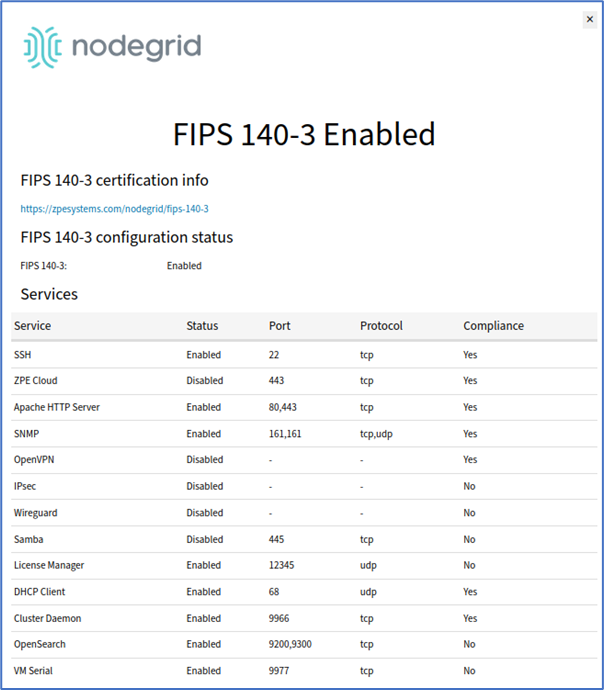
Enable FIPS 140-3 | Enabling FIPS 140-3 on a Nodegrid device ensures FIPS compliance, limiting cryptographic services to the FIPS provider for the applications that rely on OpenSSL for these services.
| Enabled |
SSH
Setting | Description | Default |
SSH allow root access |
| Disabled |
Web Service
Setting | Description | Default |
Enable HTTP access | Enables the HTTP access to the managed device. | Enabled, 80 |
Enable HTTPS access | Enables the HTTPs access to the managed device. | Enabled, 443 |
Enable HTTP/S File Repository | Enables HTTP/S file repository to store the software images.
You can enable access to the Web UI using the CLI. To do this, access the Console and run the following commands. This method is useful if a user gets locked out of the Web UI and when HTTP and HTTPS are disabled. | Disabled |
FRR
Setting | Description | Default |
Enable BGP | Activates Border Gateway Protocol (BGP) to manage routing between autonomous systems. | Enabled |
Enable ISIS | Activates ISIS protocol to support routing capabilities | Disabled |
Enable OSPFv2 | Enables OSPFv2 for IPv4 routing in dynamic network environments. | Disabled |
Enable OSPFv3 | Activates OSPFv3 to support IPv6 routing capabilities. | Disabled |
Enable PATH | Activates PATH daemon to handle installation and deletion of Segment Routing Policies | Disabled |
Enable RIP | Turns on the Routing Information Protocol (RIP) for simple, distance-vector-based routing. | Disabled |
Enable VRRP | Enables Virtual Router Redundancy Protocol (VRRP) to provide router failover and redundancy. | Disabled |
Cryptographic Protocols
Setting | Description | Default |
TLSv1.3 | Activates support for the TLS 1.3 protocol for secure communications. | Enabled |
TLSv1.2 | Enables support for the TLS 1.2 protocol for backward compatibility. | Enabled |
TLSv1.1 | Allows the use of TLS 1.1 protocol, but it is disabled by default for security reasons. | Disabled |
TLSv1 | Enables TLS 1.0 protocol, disabled by default due to known vulnerabilities. | Disabled |
Cipher Suite Level |
| Medium |
Saving the Configuration
Click Save. ZPE Cloud ensures all deployment activity is done at the device location.