Overview
TACACS+ (Terminal Access Controller Access-Control System) is a protocol that handles authentication, authorization, and accounting (AAA) services. The following diagram shows a Nodegrid Serial Console Plus (NSCP) and the Ubuntu server executing a TACACS+ server.
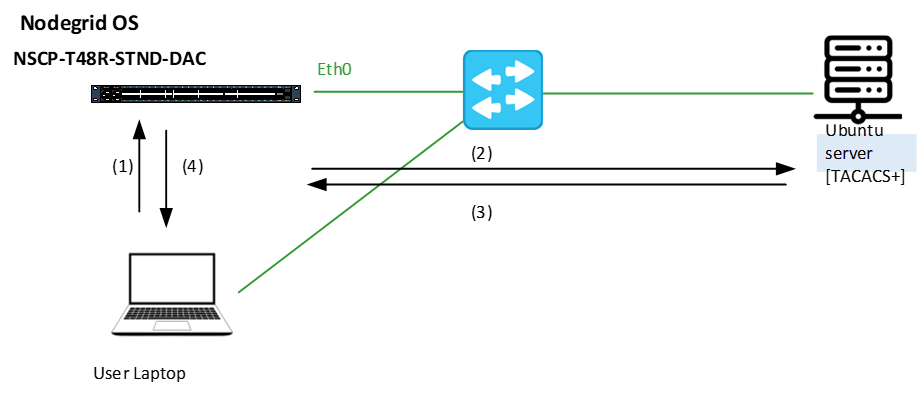
(1) and (4) | Endpoint accessing the Nodegrid device using HTTPS. |
(2) and (3) | Nodegrid sends the login request to the TACACS+ server for authentication. The TACACS+ server evaluates the request and determines whether to grant access to the Nodegrid and assigns the appropriate privilege level. |
An example of Ubuntu server executing TACACAS+ configuration is as shown:
key = test
accounting file = /var/log/tac.acct
group = tadmin {
service = raccess {
prlv-lvl = 15
}
}
group = read {
service = raccess {
prlv-lvl = 1
}
}
user = user 1 {
login = cleartext hello
member = tadmin
}
user = user 2 {
login = cleartext user 2
member = read
}
user = guest{
default service = permit
login = des guE/.mlvd58eU
}
The two user groups defined are:
tadmin, with privilege 15 and user: user 1
read, with privilege 1 and user: user 2
NOTE:
Check the syntax of the tacacs configuration, by using the command sudo service tacacs_plus check.
Check the status of the tacacs+ server, by using the command systemctl status tacacs_plus (the status given should be in green color, in state "active").
Nodegrid Configuration
Web UI:
Log in to the Nodegrid Web UI.
Navigate to Security:: Authentication:: Servers and select the Method as TACACS+.
Enter Accounting Server.
NOTE:
The accounting server is optional, and in case no accounting server is available the setting can be left blank.
.png)
Note
The fields Remote Server and Accounting Server correspond to the IP address of the Ubuntu Server. The Service, "raccess" has to match the Tacacs+ server.
Select Authorize users authenticated with ssh public key checkbox.
Enter TACACS+ Port (default: 49).
On Service drop-down, select one (PPP, Shell, raccess) (default: raccess).
Enter and confirm the secret shared with the Tacacs+ server.
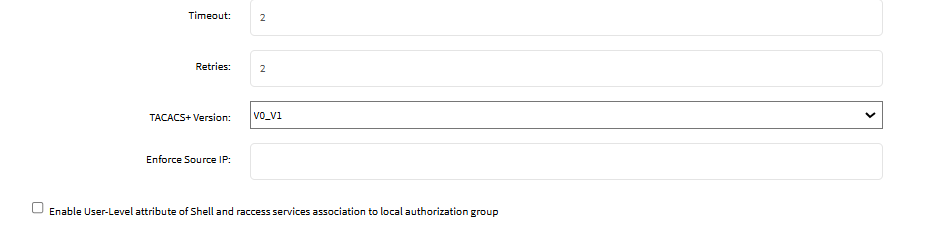
Enter Timeout (default: 2).
Enter Retries (default: 2).
On TACACS+ Version drop-down, select the appropriate TACACS+ Version.
Enter Enforce Source IP for AAA authentication (available in v5.8+).
Select Enable User-Level attribute of Shell and raccess services association to local authorization group checkbox (expands dialog with 15 User Levels).
Per instruction, “Enter local authorization group name for each User Level.”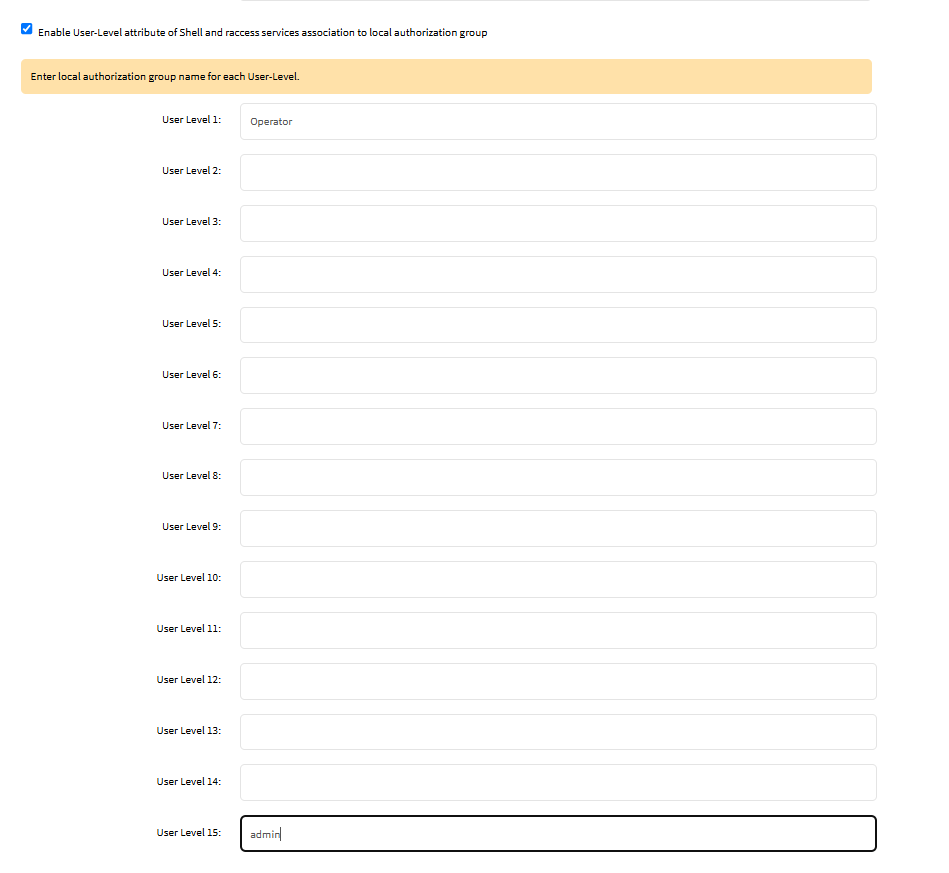
Note
In this example,
- the tacacs+ admin group "tadmin" (of privilege 15), to the local Nodegrid admin group "admin".
- the tacacs+ admin group "read" (of privilege 1), to the local Nodegrid user group "Operator"
The user added in the TACACS+ as user1 will be able to login as shown in the following figure.
CLI Configuration
Log in as admin in the CLI and type the following commands:
[admin@nodegrid /]# add settings/authentication/servers/ [admin@nodegrid {servers}]# set fallback_if_denied_access=yes [admin@nodegrid {servers}]# set method=tacacs+ [admin@nodegrid {servers}]# set remote_server=10.10.10.13 [admin@nodegrid {servers}]# set tacacs_plus_accounting_server=10.10.10.13 [admin@nodegrid {servers}]# set tacacs_plus_secret=secretkey [admin@nodegrid {servers}]# set tacacs_plus_service=raccess [admin@nodegrid {servers}]# set tacacs_plus_retries=2 [admin@nodegrid {servers}]# set tacacs_plus_timeout=2 [admin@nodegrid {servers}]# set tacacs_plus_version = v1 [admin@nodegrid {servers}]# set tacacs_plus_enable_user-level = yes [admin@nodegrid {servers}]# set tacacs_plus_user_level_1 = Operator [admin@nodegrid {servers}]# set tacacs_plus_user_level_15 = adminType show command to confirm your configuration.
[admin@nodegrid {servers}]# showSave the configuration.
[admin@nodegrid {servers}]# commitType the set command and tap tab key twice to view all the available option for configuration.
[admin@nodegrid {servers}]# set
The TACACS+ server added to Nodegrid.
NOTE
Default authentication service is raccess ( can be changed as needed )
Default value for retries and timeout is 2 ( can be changed as needed )
Default port is 49
Group level to be used in Nodegrid OS
In the Web UI and TACACS+, specify the group level to be used in the Nodegrid OS. You can configure your TACACS+ server to map two separate groups, each with the same privilege level, to two different groups on the Nodegrid OS.
Go to Security :: Authentication :: Servers :: 1.
Uncheck Enable User-Level attribute of Shell and raccess services association to local authorization group.
On the TACACS+, server, add the attribute group_name in the groups:
Go to Security :: Authorization :: Network_Admin :: Remote Groups, in the Nodegrid groups add these groups under Remote Group.