Authentication Methods
Multiple authentication methods are available. Some are simple (Pre-Shared keys and RSA keys) but with limited flexibility. Others require more initial configuration and setup which offers flexibility and consistency.
Pre-shared Keys
Pre-shared Keys provide the simplest and least secure method to secure an IPsec connection. This is a combination of characters that represent a secret. Both nodes must share the same secret. Nodegrid supports pre-shared keys with a minimum length of 32 characters. The maximum length is much higher. Due to compatibility reasons with other vendors, Nodegrid uses a 64-bit length for the examples. The longer the pre-shared key is, the more secure it is.
RSA Keys
RSA Keys or Raw RSA keys are commonly used for static configurations between single or a few hosts. The nodes are manually configured with each other’s RSA keys.
X.509 Certificates
Typically, X.509 Certificate authentications are used for larger deployments with a few to many nodes. The RSA keys of the individual nodes are signed by a central Certificate Authority (CA). The Certificate Authority maintains the trust relationship between the nodes. As needed, specific nodes can include revocation of trust. Nodegrid supports both public and private CA’s. As needed, the Nodegrid Platform can host and manage its own Certificate Authority for IPsec communication.
Connection Scenarios
IPsec supports many connection scenarios, from the basic one-to-one nodes and the more complex one-to-many nodes. Communication can be limited to the directly involved nodes. If needed, communication can be expanded to the networks access table behind the nodes. Examples are provided for some of the most common scenarios.
Host-to-Host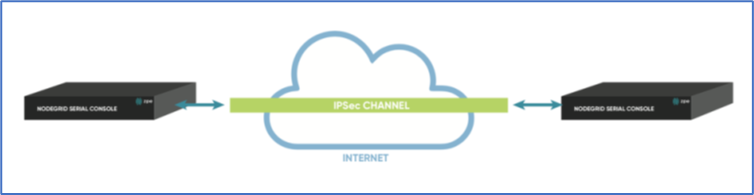
Host-to-Host communication is two nodes directly connected with a VPN tunnel. The communication is limited to direct communication between them. None of the packages are routed or forwarded. This is a point-to-point communication tunnel between two nodes.
Host-to-Site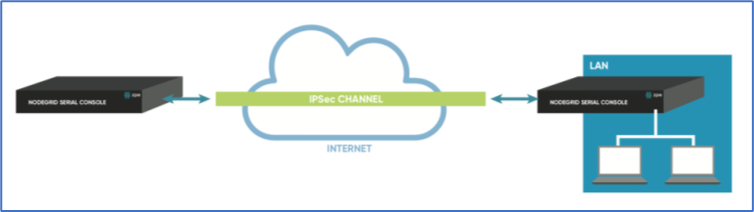
With host-to-Site, one node establishes a VPN tunnel to a second node. Communication is limited on one site to the specific node; and on the other side, limited to all devices in a range of subnet accessible by the second node.
Site-to-Site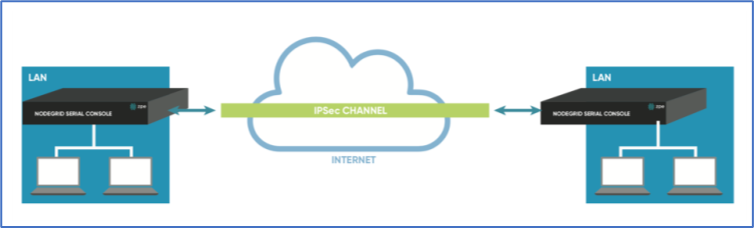
In site-to-site, the tunnel is established between two nodes. Communication can specify the subnet on both sides. This allows communication between devices on either side of the connection.
Host-to-Multi-Site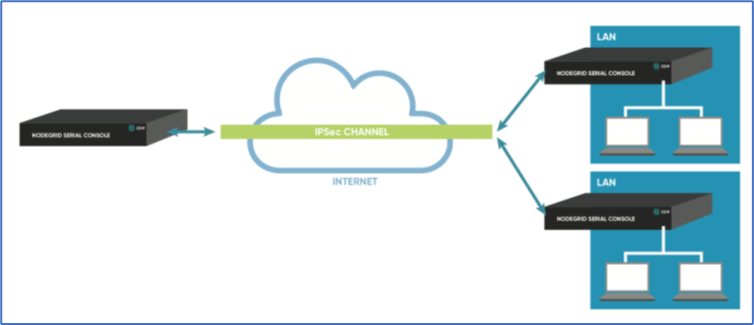
Host-to-multi-site communication is created with individual VPN connections. This is done between hosts or with specific multi-site configurations (which greatly improves scalability). Multiple nodes can connect to the same node. A typical use would be remote offices with a VPN connection to the main office. This would limit communications to the one node and devices on specified subnets in the remote locations.
Site-to-Multi-Site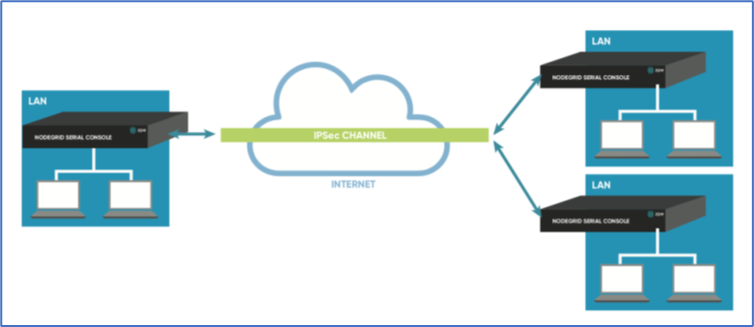
Site-to-multi-site is most common for enterprise VPN setups. Similar to host-to-multi-site, communication is allowed to the specific subnet on either side. The West node would have access to all specified subnet on any of the sites. The remote sites only can access the subnet exposed by the West node.
Keys and Certificates
Keys and Certificates
| Host to Host | Host to Site | Site to Site | Host to Multi-Site | Site to Multi-Host |
Pre-shared Keys | Possible | Possible | Possible | Possible | Possible |
RSA Key | Recommended | Recommended | Recommended | Possible | Possible |
X.509 Certificates | Recommended | Recommended | Recommended | Recommended | Recommended |