What is the SSL/TLS deep Inspection Configuration Running at the Site's Firewall
An on-site SSL/TLS deep inspection firewall configuration is a security setup where the firewall decrypts encrypted traffic to inspect it for threats, then re-encrypts it before forwarding it to its destination. This is done by having the firewall act as a "man-in-the-middle," creating two separate SSL connections: one with the client and one with the destination server. This configuration is usually set on firewall servers linked to routers in the corporate networks.
For this to work seamlessly, all user devices on the network must trust the firewall's certificate, which is typically achieved by pre-installing the certificate on company-owned devices. This is many times done by an application installed from IT running on the corporate user devices, but not so seamlessly for IT devices, since they must be managed by IT team.
The Symptom of the Problem
On ZPE Cloud, the status of the device remains as "Never Connected" or "Offline".
On NodeGrid Operating System, when navigating to Tracking :: ZPE Cloud::Device Information page, it displays the unit status as "Disconnected - Requesting Pairing".
How to Identify the Problem
Below you will find 3 scenarios that can be used to identify if the problem is occurring.
Scenario 1.
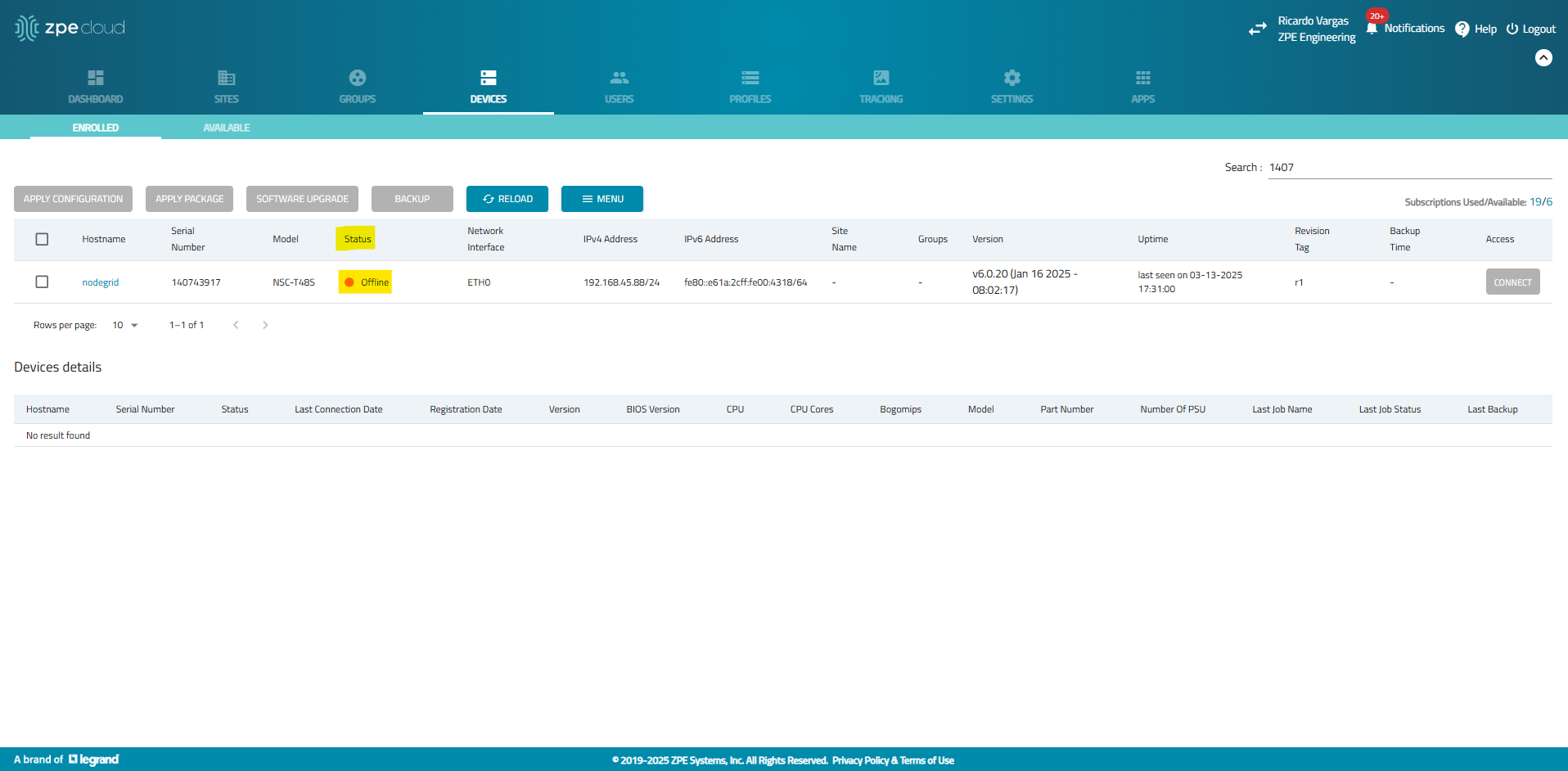
As an administrator check the device status to verify if the Status is "Offline" or "Never Connected".
Scenario 2
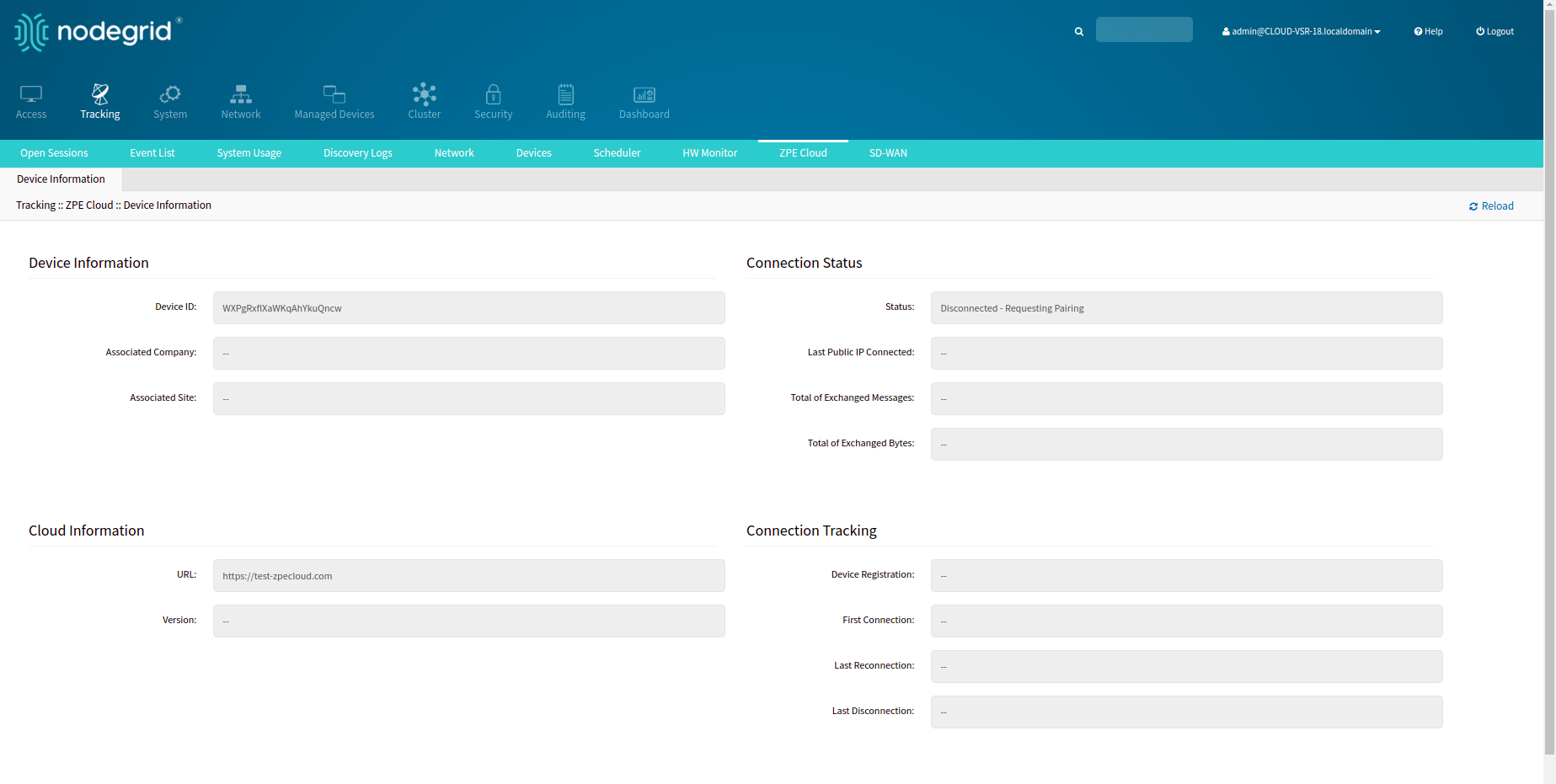
As an administrator navigate to Tracking::ZPE Cloud::Device Information and check if the Status is "Disconnected - Requesting Pairing".
Scenario 3.
Check to see if the system returns a self-signed certificate that was added to the chain of certificates after using openssl s_client -showcerts below.
For ZPE Cloud US:
openssl s_client -showcerts -servername api.astarte.zpecloud.com -connect api.astarte.zpecloud.com:443 < /dev/null;
For ZPE Cloud EU:
openssl s_client -showcerts -servername api.astarte.zpecloud.eu -connect api.astarte.zpecloud.eu:443 < /dev/null;
Replace -servername and -connect with the name of the ZPE Cloud instance being tested.
Examples of possible outputs:
Example 1:
The output of the certificate issuer is not included in the CA path (/etc/ssl/certs/< ca>.pem) and CA file (/etc/ssl/certs/ca-certificates.crt):
CONNECTED(00000003)
depth=1 C = US, O = ZScaler, CN = zscaler.net
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = US, ST = California, L = Fremont, O = "ZPE Systems, Inc.", CN = astarte.zpecloud.com
verify return:1
Example 2:
The output is a self-signed certificate in the certificate chain:
CONNECTED(00000003)
depth=1 C = US, O = ZScaler, CN = zscaler.net
verify error:num=19:self-signed certificate in certificate chain
verify return:1
depth=0 C = US, ST = California, L = Fremont, O = "ZPE Systems, Inc.", CN = astarte.zpecloud.com
verify return:1
Example 3:
The output of a working certificate:
depth=3 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root G2
verify return:1
depth=2 C = US, O = DigiCert Inc, CN = DigiCert Global G2 TLS RSA SHA256 2020 CA1
verify return:1
depth=1 C = US, O = ZScaler, CN = zscaler.net
verify return:1
depth=0 C = US, ST = California, L = Fremont, O = "ZPE Systems, Inc.", CN = *.astarte.zpecloud.com
verify return:1
Fix for the Problem
Option 1
Exclude ZPE Cloud domain/IPs from SSL traffic/deep inspection:
- Login into the Firewall service platform
- Go to SSL deep inspection/Traffic inspection
- Disable the SSL inspection for ZPE Cloud domain or NG OS IP/mac
- Login as a customer admin to ZPE Cloud
- Go to Devices::Enrolled
- Check to see if the unit is online after 1-3 minutes (Depends on the network velocity, GSM is slower)
Option 2
Add SSL traffic/deep inspection certificates signed by a known CA:
- Login into the Firewall service platform
- Go to SSL deep inspection/Traffic inspection
- Change the self-signed certificates to Let’s encrypt signed certificates
- Login as a customer admin to ZPE Cloud
- Go to Devices::Enrolled
- Check to see if the unit is online after 1-3 minutes (Depends on the network velocity, GSM is slower)
Option 3
Move your device to another network without SSL traffic/deep inspection:
- Unplug the ethernet cable and connect another ethernet cable to a new network or make your GSM a primary connection to the NodeGrid unit
- Login as a customer admin to ZPE Cloud
- Go to Devices::Enrolled
- Check to see if the unit is online after 1-3 minutes (Depends on the network velocity, GSM is slower)
Option 4
Add the SSL deep inspection self-signed certificate to the System Administrator trust store:
- Download the self-signed certificate and install if on the unit
- Via SCP:
- scp mycertificate.crt admin@192.168.10.48:/home/admin/
- Via File Manager:
- Login as admin in NG GUI
- Go to Access::Table
- Click to open File Manager
File Manager is displayed - Click on admin_home directory on File Manager
- Click to upload
- Select the certificate file from the local directory
- Click to confirm the upload
- Check if the certificate is listed on File Manager
- Via SCP:
- Login as root in NG Shell
- Move the certificate to the System Administrator trust store, under ZPE Cloud folder:
- mv /home/admin/mycertificate.crt /usr/local/share/ca-certificates/zpe-cloud-ca-certificates/;
- Update the trust store. Execute:
- update-ca-certificates -f
- Confirm that the certificate is now trusted using the prompt below:
- for ZPE Cloud US: openssl s_client -showcerts -servername api.astarte.zpecloud.com -connect api.astarte.zpecloud.com:443 < /dev/null;
for ZPE Cloud EU: openssl s_client -showcerts -servername api.astarte.zpecloud.eu -connect api.astarte.zpecloud.eu:443 < /dev/null; - Check if the output displays no error to trust certificate chain;
- for ZPE Cloud US: openssl s_client -showcerts -servername api.astarte.zpecloud.com -connect api.astarte.zpecloud.com:443 < /dev/null;
- Login as admin in NG GUI
- Be sure Enable ZPE Cloud is checked under Security::Services
- You may Disable, Save, Enable, Save the ‘Enable ZPE Cloud’ configuration to accelerate the time for the unit to show Online;
- See after 1-3 minutes the unit shows Online (Depends on the network velocity - GSM is slower -);
System Administrator trust store (under /usr/local/share/ca-certificates/) is used to add custom certificates used by the System Administrator and those certificates will be mapped to /etc/ssl/certs.
System Administrator trust store is a configuration folder, its content is deleted when a factory reset is done, except for persistent folders added as symbolic link inside this directory.
zpe-cloud-ca-certificates (/usr/local/share/ca-certificates/zpe-cloud-ca-certificates) is a persistent folder inside this trust store. A symbolic link is always mapped to a /var folder that is not affected by a factory reset. So, if it is desired, adding certificates to this directory will make it persistent (except for formatting partitions or a fresh install of the OS).
All certificates stored in the System Administrator trust store should have the PEM format and be named with the .crt extension, if not, the certificate is not going to be added to the trust store.
Example: mycertificate.crt
Acronyms
| Acronym | Meaning | Definition |
|---|---|---|
| CA | Certificate Authority | An entity that issues digital certificates to verify identities and secure communications. |
| GSM | Global System for Mobile Communications | A standard for mobile networks, commonly used for cellular data and voice communication. |
| GUI | Graphical User Interface | A visual interface that allows users to interact with software using graphical elements like windows, icons, and buttons. |
| IP | Internet Protocol | A set of rules for routing and addressing packets of data so they can travel across networks and arrive at the correct destination. |
| NG | Nodegrid | Refers to the platform or devices developed by ZPE Systems for secure access and automation. |
| OS | Operating System | Software that manages hardware and software resources on a device. |
| PEM | Privacy Enhanced Mail | A format for storing and transmitting cryptographic keys and certificates, typically using .pem or .crt extensions. |
| SCP | Secure Copy Protocol | A method for securely transferring files between computers over SSH. |
| SSL | Secure Sockets Layer | A protocol for encrypting data between web servers and browsers; now largely replaced by TLS. |
| TLS | Transport Layer Security | A cryptographic protocol that ensures privacy and data integrity between communicating applications. |