Nodegrid can be configured as a VPN server. By default, this is disabled. Depending on the configuration, multiple files are required and must be available in the /etc/openvpn/CA folder. 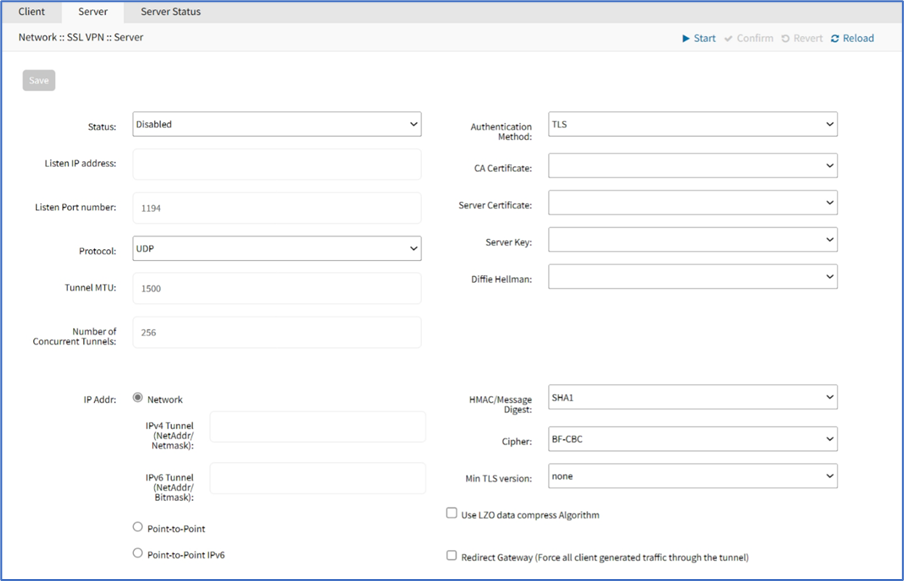
Configure SSL VPN Server Details
- Go to Network :: VPN drop-down :: VPN :: Server.
- On Status drop-down, select one (after configuration as a VPN server, must be enabled).
- Enabled
- Disabled (default)
- Enter details:
- Listen IP address (if defined, server only responds to client requests coming in this interface)
- Listen Port number (listening port for incoming connections - default: 1194)
- Protocol drop-down, select one (UDP, TCP, UDP IPv6, TCP IPv6)
- Tunnel MTU (default: 1500)
- Number of Concurrent Tunnels (default: 256)
- On Authentication Method menu, enter details (different fields are displayed according to selection).
- TLSselection:
- CA Certificate drop-down, select one
- Server Certificate drop-down, select one
- Server Key drop-down, select one
- Diffie Hellman drop-down, select one
- Static Keyselection:
- Secret drop-down, select one
- Diffie Hellman drop-down, select one
- Passwordselection:
- CA Certificate drop-down, select one
- Server Certificate drop-down, select one
- Server Key drop-down, select one
- Diffie Hellman drop-down, select one
- Password plus TLSselection:
- CA Certificate drop-down, select one
- Server Certificate drop-down, select one
- Server Key drop-down, select one
- Diffie Hellman drop-down, select one
- TLSselection:
- On IP Address menu (display changes based on selection) this configures IP address settings for the tunnel:
- Networkradio button:
- IPv4 Tunnel (NetAddr/Netmask)
- IPv6 Tunnel (NetAddr/Netmask)
- Point to Pointradio button:
- Local Endpoint (Local IP)
- Remote Endpoint (Remote IP)
- Point To Point IPv6radio button:
- Local Endpoint (Local IPv6)
- Remote Endpoint (Remote IPv6)
- Networkradio button:
- Enter details:
- HMAC/Message Digest drop-down (select HMAC connection algorithm)
- Cipher drop-down (select connection cipher algorithm)
- Min TLS version drop-down, select one (None, TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3)
- Use LZO data compress Algorithm checkbox (all tunnel traffic is compressed)
- Redirect Gateway (Force all client generated traffic through the tunnel) checkbox (all traffic from client is forced through the tunnel).
- Click Save.
Edit VPN Server Details
- Go to Network :: VPN drop-down :: VPN :: Server.
- Make modifications, as needed.
- Click Save.