This section outlines the steps for generating certificates using the ACME protocol in Nodegrid. The process includes creating a Certificate Signing Request (CSR), submitting it for signing through a Certificate Authority (CA), and handling the HTTP-01 and DNS-01 challenges.
Using Web UI:
Sign in with ACME (HTTP-01)
Log in to the Nodegrid web UI.
Navigate to Security:: Certificates.
Create a Certificate Signing Request (CSR).
Navigate to the recently created CSR.
Click Sign with ACME.
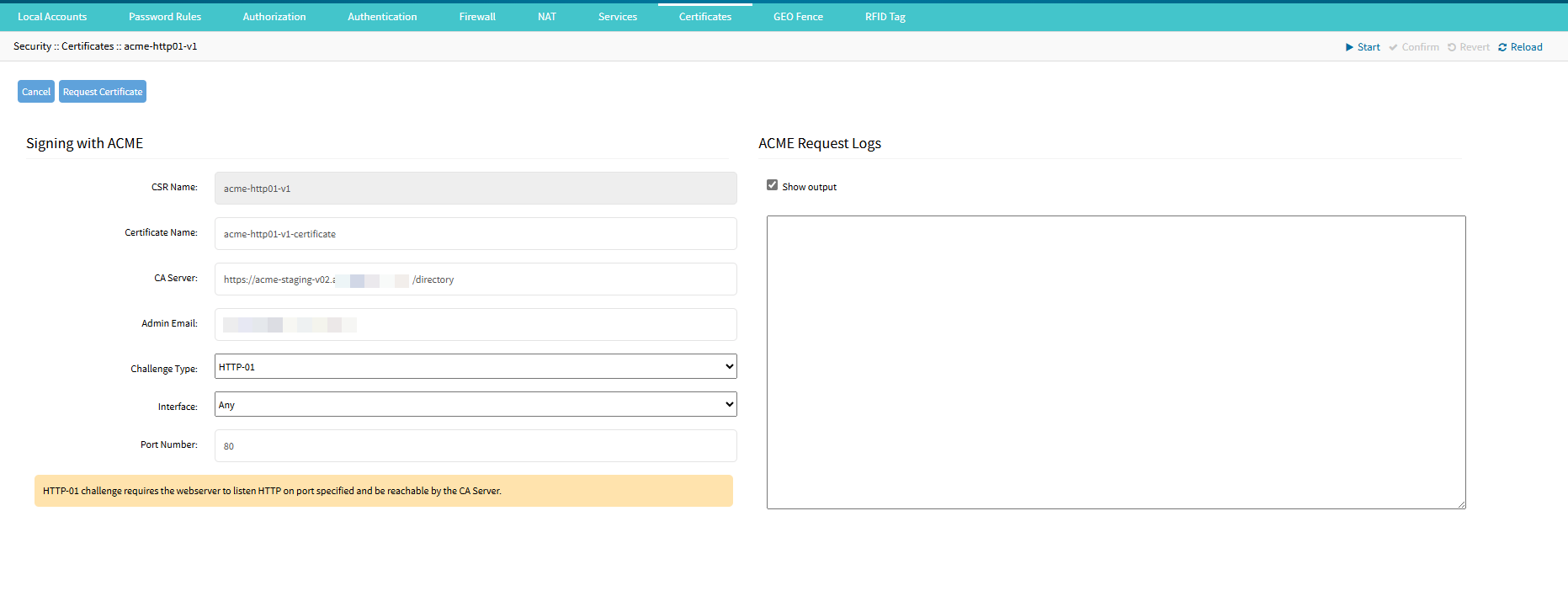
Enter the following fields. Some of the fields are auto-populated from the CSR.
CSR Name: Auto-populated from the CSR(read-only).
Certificate Name: Name of the certificate after signing in.
CA Server: The Certificate Authority server URL is used for the certificate validation.
Admin Email: Email address of the user to issue the certificate.
Interface: The network interface on Nodegrid that CA should reach to validate the certificate.
Port Number: The port number (on the specified interface) that CA should reach to validate the certificate.
NOTE
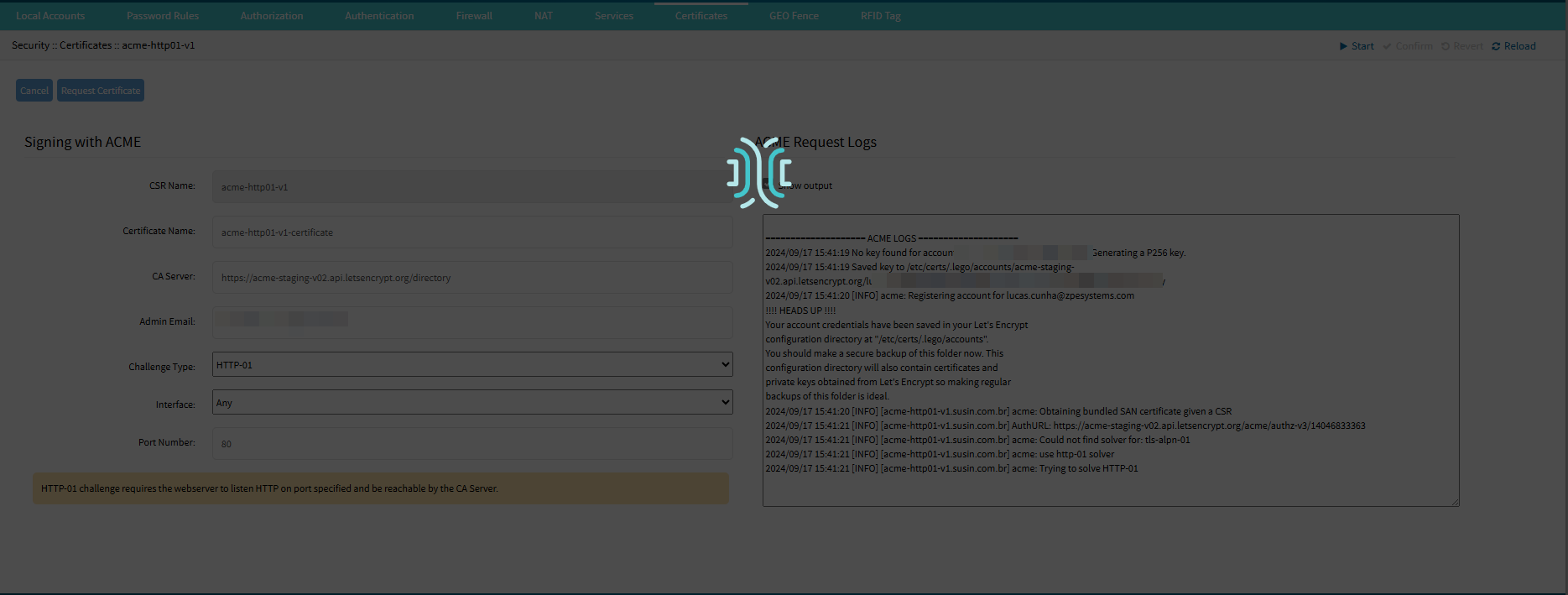
Users can enable the ACME Request Logs if needed (Recommended).
Click Request Certificate. The user is redirected to the Certificates Table with the new certificate generated.
Sign in with ACME (DNS-01)
Log in to the Nodegrid web UI.
Navigate to Security :: Certificates.
Create a Certificate Signing Request (CSR).
Navigate to the recently created CSR.
Click Sign with ACME.
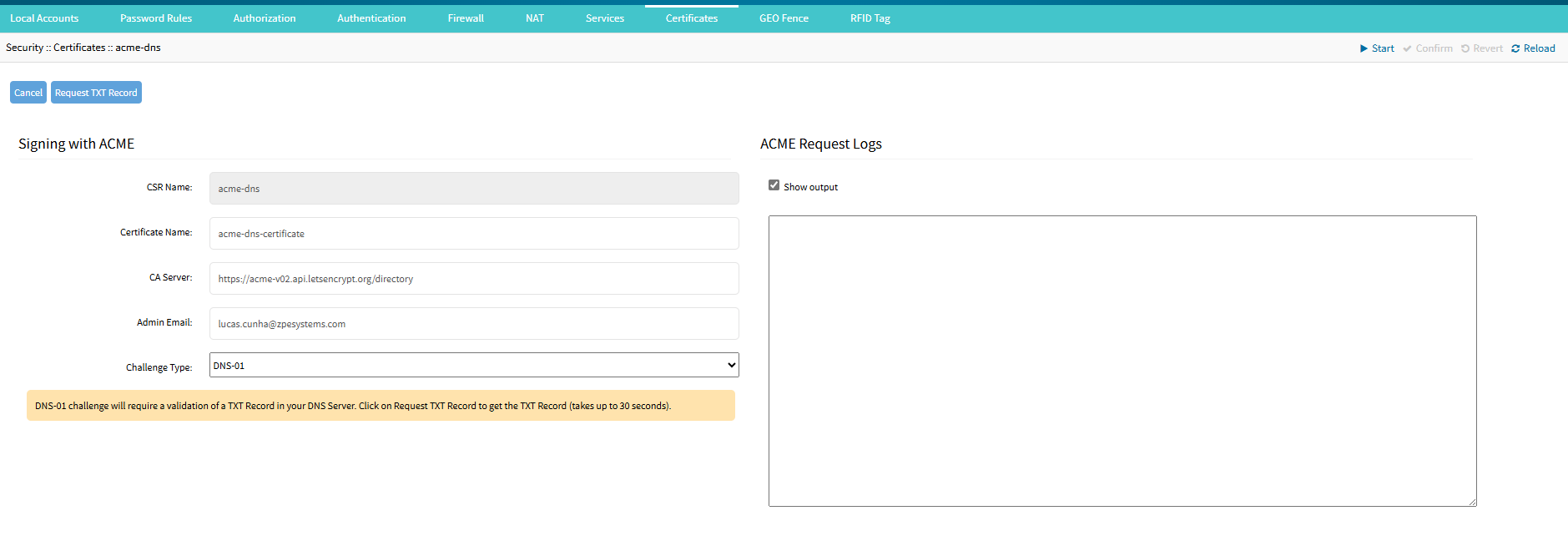
Enter the following fields. Some of the fields are auto-populated from the CSR.
CSR Name: Auto-populated from the CSR(read-only).
Certificate Name: Name of the certificate after signing in.
CA Server: The Certificate Authority server URL is used for the certificate validation.
Admin Email: Email address of the user to issue the certificate.
NOTE
Users can enable the ACME Request Logs if needed (Recommended).
Click on Request TXT Record. The page will reload with a new field named TXT Record.
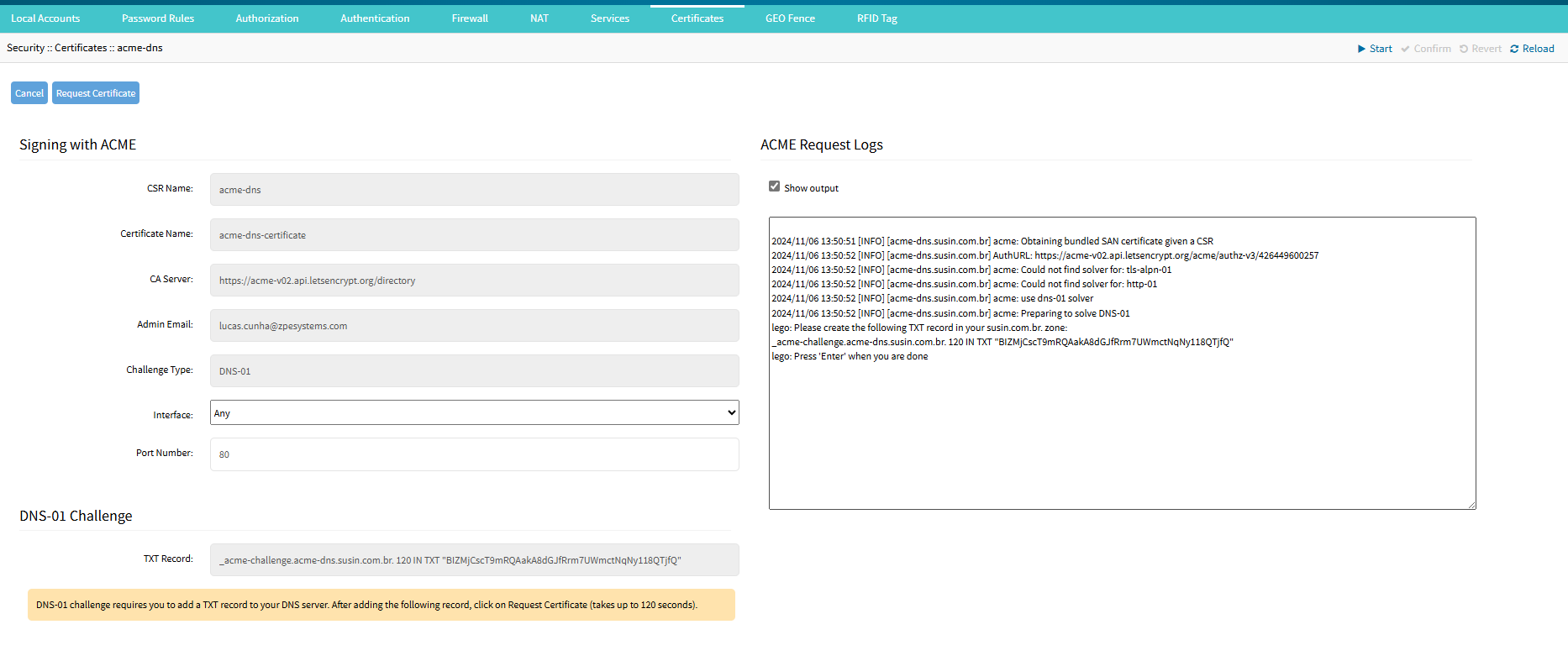
User should use the given TXT Record and paste on the DNS provider so that DNS-01 request the certificate to the CA server.Once you paste the TXT Record and save it, click Request Certificate. The page reloads with a new field named TXT Record. Enabling the ACME Request Logs makes easier to understand on which process the ACME is running.
If successful, you will be redirected to the Certificates Table with the new certificate generated.
Using CLI
acme_sign (HTTP-01)
Access /settings/certificates:
[admin@nodegrid acme-http]# cd /settings/certificates [admin@nodegrid certificates]# show name common name status type issuer issued on expires on used by ==================== =========================== ====== ===================== ===================================================================== ======================== ======================== ========= nodegrid-default e41a2c00752c Valid Signed Certificate ZPE Systems Inc e41a2c00752c Nov 1 14:55:21 2024 GMT Feb 4 14:55:21 2027 GMT Webserver acme-http acme-http.example.com Valid Signing Request (CSR) - - -Create a valid CSR (Certificate Signing Request).
Navigate to the recently created CSR.
Type acme_sign.
[admin@nodegrid certificates]# cd acme-http [admin@nodegrid acme-http]# acme_signSelect the ACME Challenge type (default is HTTP-01) and acme_sign again.
[admin@nodegrid {acme-http}]# show challenge_type = http-01 Set the ACME challenge type before proceeding with 'next' command. [admin@nodegrid {acme-http}]# nextEnter all the fields (some are read from the CSR):
CSR Name: Auto-populated from the CSR(read-only).
Certificate Name: Name of the certificate after signing in.
CA Server: The Certificate Authority server URL used for the certificate validation.
Admin Email: Email address of the user to issue the certificate.
Interface: The network interface on Nodegrid that CA should reach to validate the certificate.
Port Number: The port number (on the specified interface) that CA should reach to validate the certificate.
[admin@nodegrid {acme-http}]# set certificate_name=acme-http-certificate [admin@nodegrid {acme-http}]# show csr name: acme-http certificate_name = acme-http-certificate ca_server = https://acme-staging-v02.api.letsencrypt.org/directory admin_email = lucas.cunha@zpesystems.com challenge type: HTTP-01 interface = any port_number = 80 HTTP-01 challenge requires the webserver to listen HTTP on port specified and be reachable by the CA Server. DNS-01 challenge will require a validation of a TXT Record in your DNS Server. Click on Request TXT Record to get the TXT Record (takes up to 30 seconds).
Type request_certificate.
[admin@nodegrid {acme-http}]# request_certificate [admin@nodegrid acme-http]# cd .. [admin@nodegrid certificates]# show name common name status type issuer issued on expires on used by ===================== =========================== ====== ========================= ===================================================================== ======================== ======================== ========= nodegrid-default e41a2c00752c Valid Signed Certificate ZPE Systems Inc e41a2c00752c Nov 1 14:55:21 2024 GMT Feb 4 14:55:21 2027 GMT Webserver acme-http-certificate acme-http.example.com Valid Signed Certificate (ACME) (STAGING) Let's Encrypt (STAGING) Counterfeit Cashew R10 Nov 6 16:01:53 2024 GMT Feb 4 16:01:52 2025 GMT - acme-http acme-http.example.com Valid Signing Request (CSR) - - - [admin@nodegrid certificates]# - - -
acme_sign (DNS-01)
Access /settings/certificates.
[admin@nodegrid certificates]# cd /settings/certificates [admin@nodegrid certificates]# show name common name status type issuer issued on expires on used by ===================== =========================== ====== ========================= ===================================================================== ======================== ======================== ========= nodegrid-default e41a2c00752c Valid Signed Certificate ZPE Systems Inc e41a2c00752c Nov 1 14:55:21 2024 GMT Feb 4 14:55:21 2027 GMT Webserver acme-dns acme-dns.example.com Valid Signing Request (CSR) -Create a valid CSR (Certificate Signing Request).
Navigate to the recently created CSR.
Type acme_sign.
[admin@nodegrid certificates]# cd acme-dns [admin@nodegrid acme-dns]# acme_signSelect the ACME Challenge type (default is HTTP-01) and acme_sign again.
[admin@nodegrid {acme-dns}]# show challenge_type = http-01 Set the ACME challenge type before proceeding with 'next' command. [admin@nodegrid {acme-dns}]# set challenge_type=dns-01 [admin@nodegrid {acme-dns}]# nextEnter all the fields (some are read from the CSR):
CSR Name: Auto populated from the CSR(read-only).
Certificate Name: Name of the certificate after signing in.
CA Server: The Certificate Authority server URL used for the certificate validation.
Admin Email: Email address of the user to issue the certificate.
[admin@nodegrid {acme-dns}]# set certificate_name=acme-dns-certificate [admin@nodegrid {acme-dns}]# show csr name: acme-dns certificate_name = acme-dns-certificate ca_server = https://acme-staging-v02.api.letsencrypt.org/directory admin_email = lucas.cunha@zpesystems.com challenge type: DNS-01 interface = any port_number = 80 HTTP-01 challenge requires the webserver to listen HTTP on port specified and be reachable by the CA Server. DNS-01 challenge will require a validation of a TXT Record in your DNS Server. Click on Request TXT Record to get the TXT Record (takes up to 30 seconds).
Type request_certificate. The page reloads with a new field named TXT Record.
[admin@nodegrid {acme-dns}]# request_txt_record [admin@nodegrid {acme-dns}]# show csr name: acme-dns certificate name: acme-dns-certificate ca server: https://acme-staging-v02.api.letsencrypt.org/directory admin email: lucas.cunha@zpesystems.com challenge type: DNS-01 interface = any port_number = 80 txt record: _acme-challenge.acme-dns.example.com. 120 IN TXT "WBtpuD6iqqjXIpnHqX3yhg03QzWT66SiZ1F0zyAitmY" DNS-01 challenge requires you to add a TXT record to your DNS server. After adding the following record, click on Request Certificate (takes up to 120 seconds). request log: 2024/11/06 14:08:29 [INFO] [acme-dns.example.com] acme: Obtaining bundled SAN certificate given a CSR 2024/11/06 14:08:30 [INFO] [acme-dns.example.com] AuthURL: https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/14779174313 2024/11/06 14:08:30 [INFO] [acme-dns.example.com] acme: Could not find solver for: tls-alpn-01 2024/11/06 14:08:30 [INFO] [acme-dns.example.com] acme: Could not find solver for: http-01 2024/11/06 14:08:30 [INFO] [acme-dns.example.com] acme: use dns-01 solver 2024/11/06 14:08:30 [INFO] [acme-dns.example.com] acme: Preparing to solve DNS-01 lego: Please create the following TXT record in your example.com. zone: _acme-challenge.acme-dns.example.com. 120 IN TXT "WBtpuD6iqqjXIpnHqX3yhg03QzWT66SiZ1F0zyAitmY" lego: Press 'Enter' when you are doneNOTE
Copy and paste the TXT Record here on the DNS provider so that the DNS-01 requests the certificate to the CA server.
The ACME logs are activated by default in CLI. Users can however double check the ACME client logs and as well the same TXT record provided.
After copying and pasting the TXT Record, type Request Certificate again. The user is redirected to the Certificates Table with the new certificate generated.
[admin@nodegrid {acme-dns}]# request_certificate [admin@nodegrid acme-dns]# cd .. [admin@nodegrid certificates]# show name common name status type issuer issued on expires on used by ===================== =========================== ====== ========================= ===================================================================== ======================== ======================== ========= nodegrid-default e41a2c00752c Valid Signed Certificate ZPE Systems Inc e41a2c00752c Nov 1 14:55:21 2024 GMT Feb 4 14:55:21 2027 GMT Webserver acme-dns-certificate acme-dns.example.com Valid Signed Certificate (ACME) (STAGING) Let's Encrypt (STAGING) Counterfeit Cashew R10 Nov 6 16:16:44 2024 GMT Feb 4 16:16:43 2025 GMT - acme-dns acme-dns.example.com Valid Signing Request (CSR) - - - - [admin@nodegrid certificates]#