The ACME (Automated Certificate Management Environment) is an industry-standard protocol that enables automatic issuance, renewal, and revocation of SSL/TLS certificates. The protocol uses Certificate Authority (CA) servers, such as Let’s Encrypt, Google Trust Services, and SSL.com to exchange certificates. An ACME client, which is built into the Nodegrid device is required to communicate with the CA server.
NOTE: While selecting the CA server, ensure that it is compatible with the ACME protocol and that the client successfully communicates with the CA.
The ACME protocol uses verification methods such as HTTP-01 (verifying through an HTTP file) and DNS-01 (verifying through a DNS record) to validate that you control the domain names in the certificate.
HTTP-01: The HTTP-01 method is the most commonly used verification process in the ACME protocol. It requires a reachable Web server.
DNS-01: The DNS-01 method is used if your device is not directly accessible from the internet such as when it is behind a NAT (without port forwarding) or within a private network (the CA cannot reach your web server to verify ownership).
To complete the verification process in such cases, you will need to add a TXT record to your domain’s DNS settings. This method ensures secure verification even when your server is not publicly accessible.
After the initial verification process (create CSR and sign in with ACME), the Nodegrid device (ACME client) communicates with the CA server to request the certificate. Once verified, the CA proceeds with issuing the certificate. The following illustration lists these steps. In this example, the CA server includes a built-in ACME server. The server requests certificates, generates token, and issues certificates. If your CA server does not have a built-in ACME server, you must use a proxy server to facilitate communication between the Nodegrid client and the CA server.
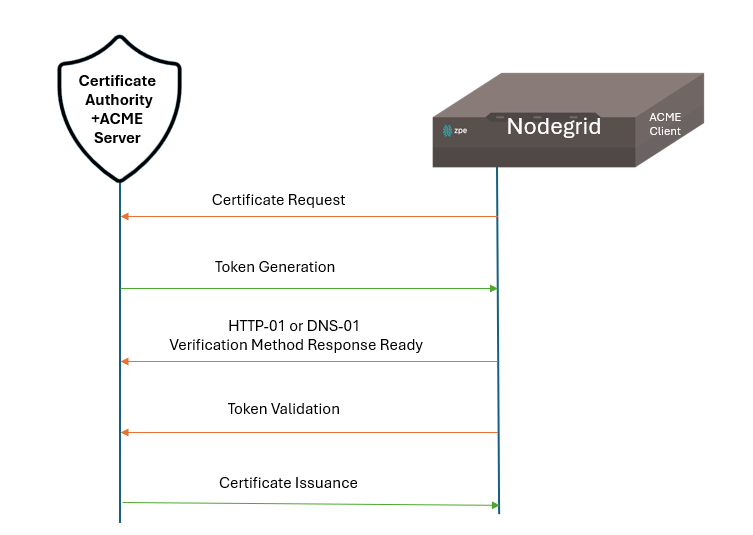
Process | Description |
|---|---|
Certificate Request | The ACME Client sends the certificate request to the Certificate Authority. |
Token Generation | The Certification Authority (CA) generates a token to ACME client (Nodegrid). HTTP-01 Method: This method includes a token that the client needs to respond to. The ACME client obtains a token from the CA server and puts a file in the Web server. The CA server then retrieves this file. If the validation is successful, the certificate is issued. If not, revalidation happens with a new certificate. DNS-01 Method:
For example, if the DNS TXT record for the domain http://example.com with the name "_acme-challenge" and the value "generated-token", the DNS record would look like this: |
Token Validation | HTTP-01 Method: After the ACME client notifies the CA that the file is ready, the CA attempts to retrieve it. If the client's web server provides the expected responses during validation, the process is successful, and the certificate is issued. DNS-01 Method: The CA server queries the DNS for the TXT record. If the validation is successful, the certificate is issued. |
Certificate Issuance | The CA issues the SSL/TLS certificate if the verification is completed successfully.
|
Cleanup (Optional) | The user can remove the verification file from the web server after the certificate is issued. |