This connection type implements the Media Access Control Security (MACSec) protocol, IEEE 802.1AE-2006, along with MACSec Key Agreement (MKA) protocol, IEEE 802.1X-2010, to provide secure communications on Ethernet links (layer 2). Together with MKA, it is possible to configure CKN/CAK fallback keys, such that the connection switches to a secondary key in case of mismatch of the primary. This allows for key rotation on both sides of the connection with limited connectivity interruption and automatic restablishment.
MACSec is not supported on NSR-Lite backplane0 if peer is connected on a switch expansion card NSR-16ETH-EXPN, NSR-16SFP-EXPN or NSR-8ETH-POE-EXPN
MACSec is only supported on NSR-Lite backplane0 if switch expansion cards are NSR-8SFP-EXPN
MACSec is not supported on NSR / NSR-Lite backplane0/backplane1 if MACSec peer is connected on a switch interface which is already running IEEE 802.1x
When fallback keys are configured and the key fallback happens, a link outage between 2.5 and 6 seconds is expected
- Go to Network :: Connections.
- Click Add (displays dialog).
- Enter Name.
- On Type drop-down, select MACSec (dialog changes).
- Enter Description (optional).
- If the Connect Automatically checkbox is selected, the connection is automatically established at system startup.
- Set as Primary Connection checkbox (defines interface as the primary connection. Only one interface can be the primary.)
- If the Block Unsolicited Incoming Packets checkbox is selected, firewall rules will be created to automatically block all inbound connections on the interface.
- In the MACsecmenu, select:
- Parent Interface: the existing OS interface that the new MACSec interface will be bound to
- Interface: the name of the new interface to be created for the MASec connection. If empty, the name will be macsecN, where N is a number starting at 0 and automatically incremented.
- MKA CKN: the MACsec Key Agreement Connectivity Association Key Name. Up to 64 hexadecimal characters that must be the same for all the MACSec participants
- MKA CAK: the MACsec Key Agreement Connectivity Association Key. Up to 32 hexadecimal characters that must be the same for all the MACSec participants
- Port: the port number to be used in the SCI (Secure Channel Identifier).
- Encrypt traffic: when selected, layer 2 traffic through this interface will be encrypted using the configured keys
- Fallback MKA CKN (optional): When set, the connection will switch to this MKA CKN in case of a mismatch in the primary MKA key between the participants of the MACSec connection. (see "Recommended key rotation procedure" section below).
- Fallback MKA CAK (optional): When set, the connection will switch to this MKA CAK in case of a mismatch in the primary MKA key between the participants of the MACSec connection. (see "Recommended key rotation procedure" section below).
- In IPv4 Mode menu, enter details:
- No IPv4 Address radio button
- DHCP radio button
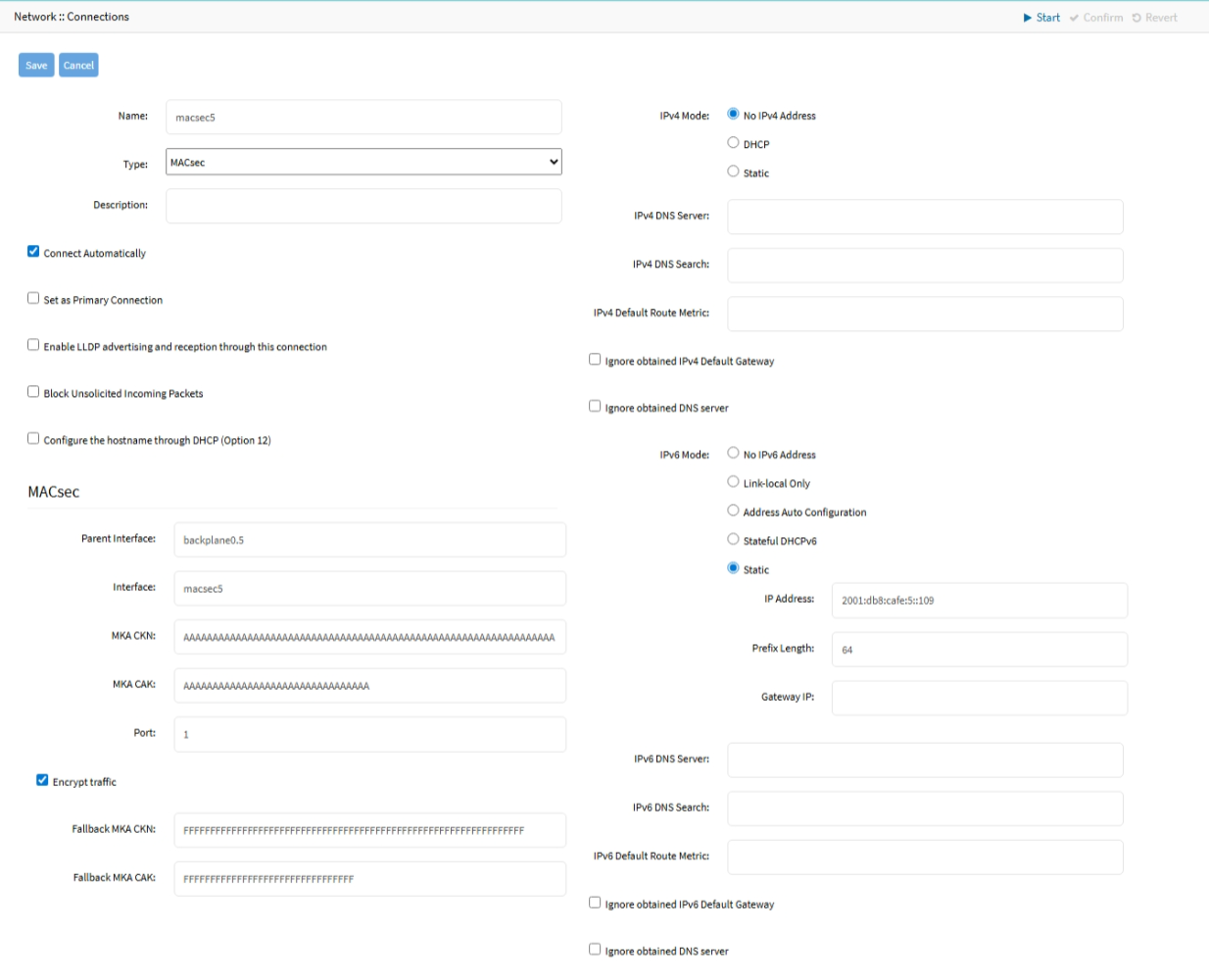
- Static radio button (if selected, expands dialog). Enter IP Address, BitMask. and (optional) Gateway IP.
- (optional) IPv4 DNS Server
- IPv4 DNS Search (defines a domain name for DNS lookups)
- IPv4 Default Route Metric
- Ignore obtained IPv4 Default Gateway checkbox
- Ignore obtained DNS server checkbox
- In IPv6 Mode menu, enter details:
- No IPv6 Address radio button
- Link local Only radio button.
- Address Auto Configuration radio button
- Stateful DHCPv6 radio button
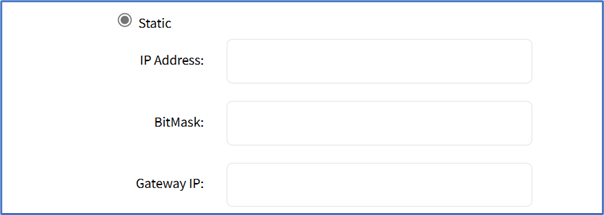
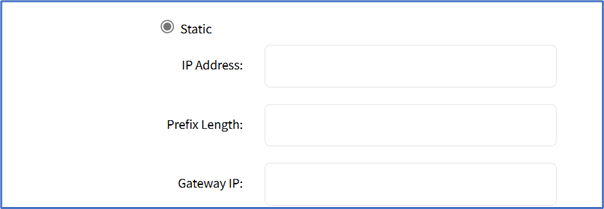
- If Static radio button is selected (displays menu). Enter IP Address, Prefix Length, and (optional) Gateway IP.
- No IPv6 Address radio button
- (optional) Enter IPv6 DNS Server.
- IPv6 DNS Search (defines domain name for DNS lookups)
- IPv6 Default Route Metric
- Ignore obtained IPv6 Default Gateway checkbox
- Ignore obtained DNS server checkbox
- Click Save.
Recommended key rotation procedure
When fallback keys are configured, the following procedure is recommended to rotate the encryption keys on the MACSec participants without losing connectivity.
Repeat the following procedure (1.a. through 1.d.) on each MACSec participant:
Copy MKA CKN to fallback MKA CKN
Copy MKA CAK to fallback MKA CAK
Commit
Main and fallback MKA are equal now
Create a new MKA (CKN and CAK)
Repeat the following procedure (3.a. through 3.b.) on each MACSec participant:
Set the new MKA CKN/CAK
Commit
Create a new fallback MKA (CKN and CAK)
Repeat the following procedure (5.a. through 5.b.) on each MACSec participant:
Set new fallback MKA CKN/CAK
Commit
All MACSec participants will be using the new main MKA now