Configure SSO with Azure AD
ZPE Cloud offers a user-friendly solution for integrating Azure Active Directory (Azure AD) as a Single Sign-On Identity Provider. This seamless integration enables users to access ZPE Cloud effortlessly while enforcing all security policies established in Azure Active Directory, including the Multi-Factor Authentication (MFA).
In this article, you'll learn how to:
Configure ZPE Cloud App in Azure - Part 1
The following configuration steps are the guidelines on how an SSO provider can be created on Microsoft Azure.
Log in to the Microsoft Azure Portal.
Navigate to Entra ID.
Navigate to Enterprise applications.
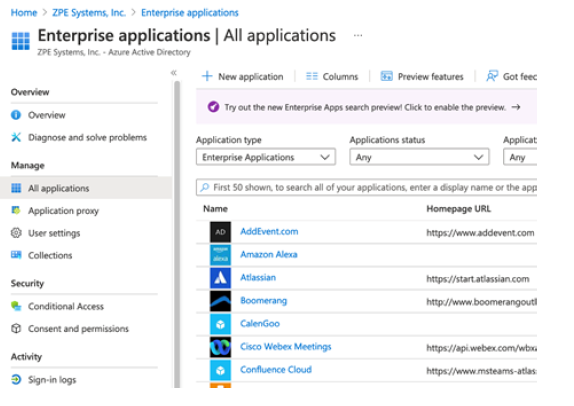
Click New application to create a new application.
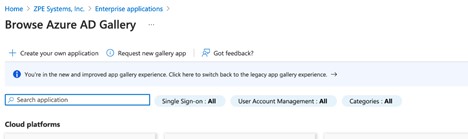
Click Create your own application to create a ZPE Cloud SSO application.
Provide a Name for the application, the recommended names are ZPE Cloud or ZPECloud EU.
Select Integrate any other application you don't find in the gallery (Nongallery).
Assign users and groups
Click Option.
Assign specific Users or User Groups that can log in using this app. These users can only log in to ZPE Cloud.
Set up a single sign-on
Click the option Single Sign-on.
Select SAML.
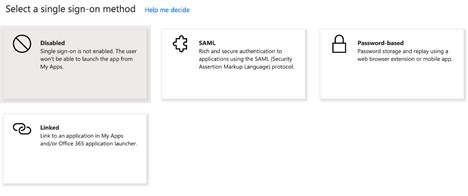
Click to edit the Basic SAML Configuration.
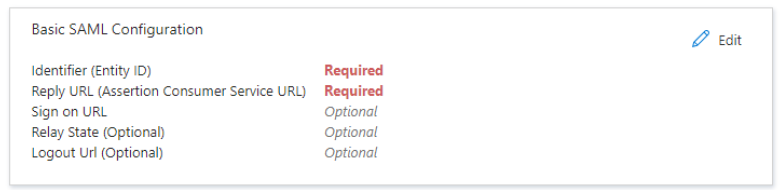
Add the Identifier (Entity ID) and the Reply URL (Assertion Consumer Service URL).
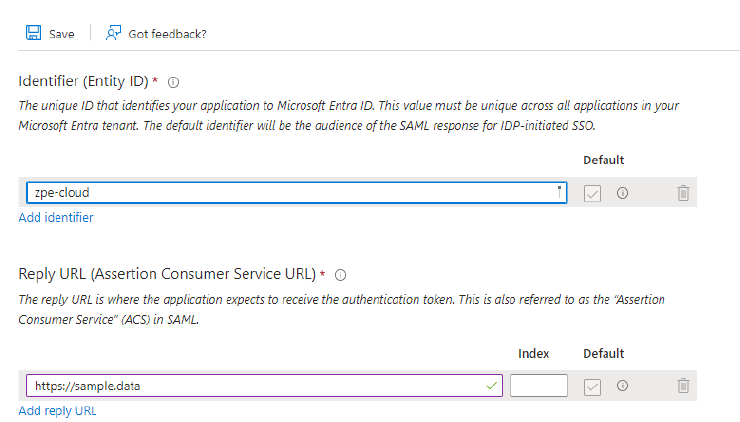
Note:
The Reply URL is a temporary placeholder. Once we generate the Metadata XML file, we'll retrieve the correct value from ZPE Cloud.
Click to edit Attributes & Claims.
Click the Add New Claim option and add the following claims:
Name : firstName , Source Attribute: user.givenname
Name : lastName , Source Attribute: user.surname
Name : memberOf , Source Attribute: “Administrator“
Name : timeout, Source Attribute: 600
Name : emailaddress, Source Attribute: user.mail
Note:
All the fields are case-sensitive, ensure that you specify the same way as they are mentioned here. For example, firstName, lastName, memberOf
The
memberOfvalue must correspond to an existing group name in ZPE Cloud. By default, a new organization includes two groups: Administrator and User. If a user is not assigned a valid group through SSO, or if no group is specified, they will be placed into the User group.
Download the Federation Metadata XML.
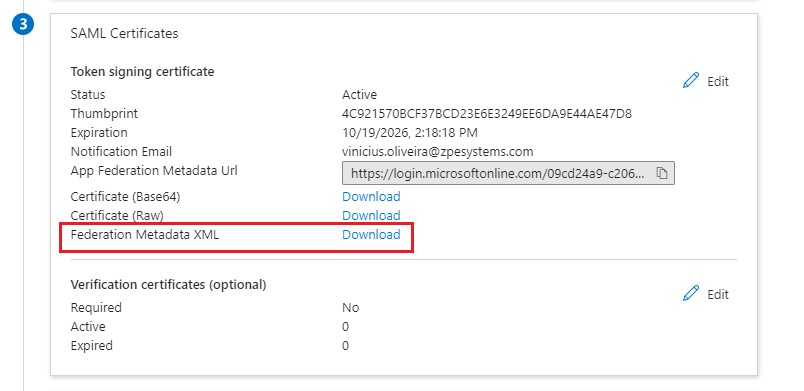
Configure Azure SSO on ZPE Cloud
Log in to the ZPE Cloud account with an Administrator account.
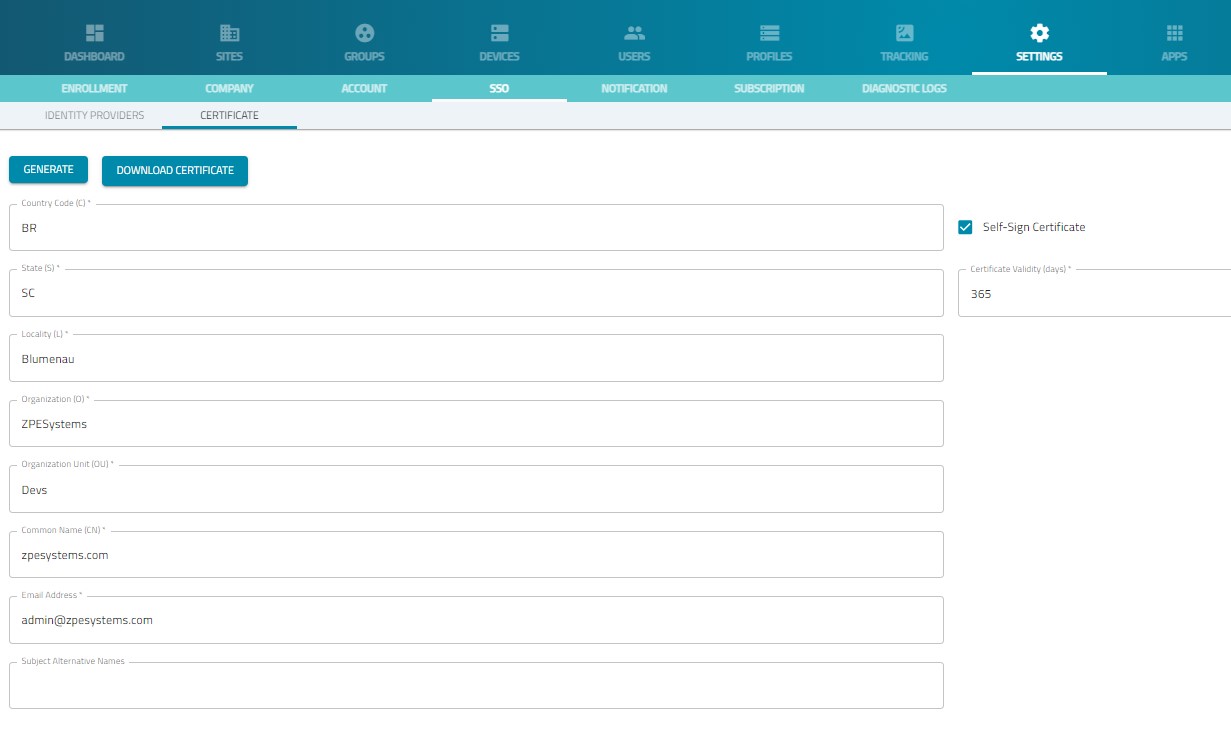
(Optional) SSO providers require a signed Logout request. For this, a certificate needs to be created. This can be a self-sign certificate or can be a signed certificate.
To create a Certificate:
navigate to Settings > SSO >Certificate and provide the following values:
Country Code: 2-letter country code for your company location
State: state for your company location
Location: location for your company location
Organization: typically company name
Organization Unit: additional OU
Common Name: recommended value: zpecloud.com or zpecloud.eu.
Email Address: email address of the Administrator.
Subject Alternative Name: same as Common Name, recommended value: zpecloud.com or zpecloud.eu.
For a Self-Signed Certificate, enable Self-Sign Certificate. Provide a value for Certificate Validity (days)
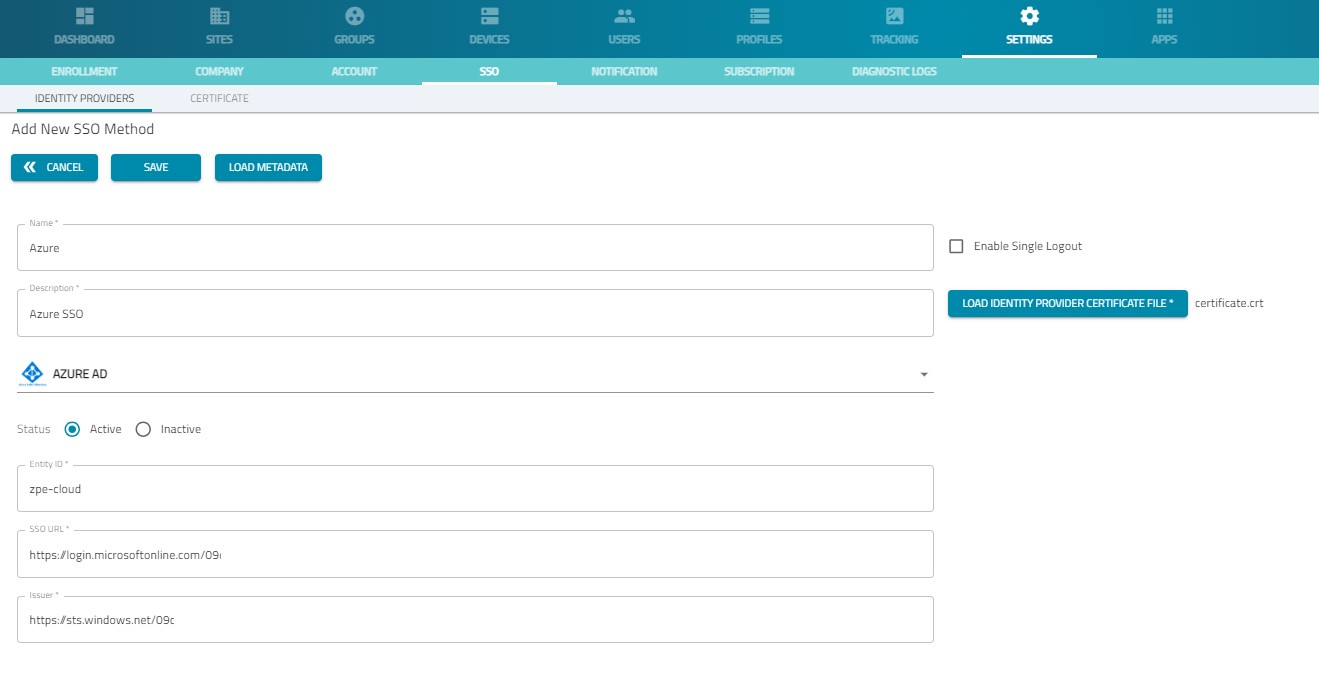
To create the SSO, navigate to Settings > SSO, and click Add.
Name: use the same value that was used in the Reply URL on Azure, the recommended value is azure
Entity ID: use the same value that was used in the Entity ID on Azure, the recommended value is zpe-cloud or zpe-cloud-eu.
Click LOAD METADATA and select the downloaded Federation MetadataXML file from Azure.
Select Enable Single Logout.
Click Save.
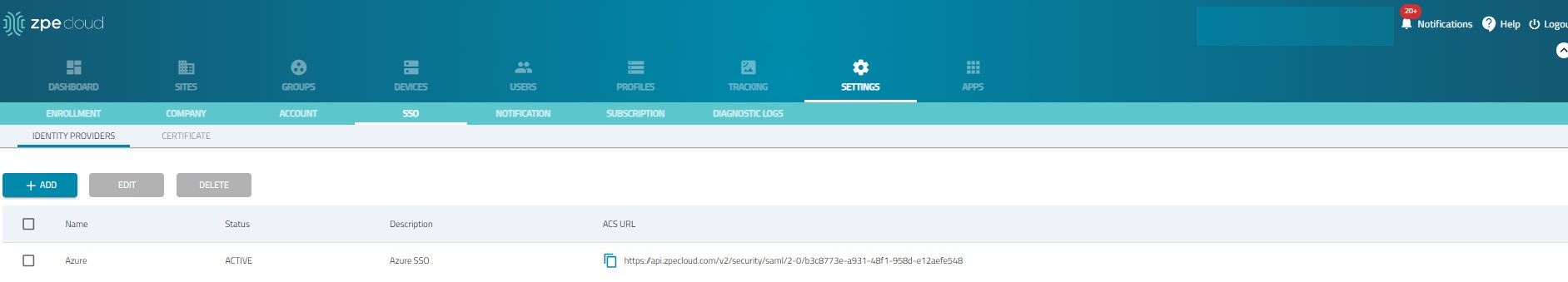
Copy the ACS URL.
Configure ZPE Cloud app in Azure - Part 2
Log in to the Azure portal, and go to your ZPE Cloud Enterprise Application Single Sign-on tab.
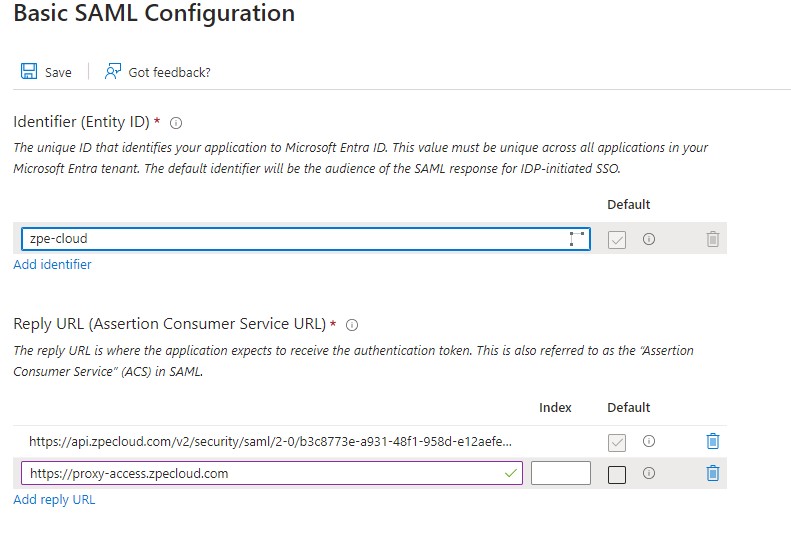
Add the ACS URL.
Click Add Reply URL and add a secondary with https://proxy-access.zpecloud.com or https://proxy-access.zpecloud.eu
The https://proxy-access.zpecloud.com or https://proxy-access.zpecloud.eu is used to set up the remote access SSO option.Click Save. The configuration is complete, you should be able to access ZPE Cloud using SSO.
(Optional) Configure ZPE Cloud SSO for Remote Access to Devices
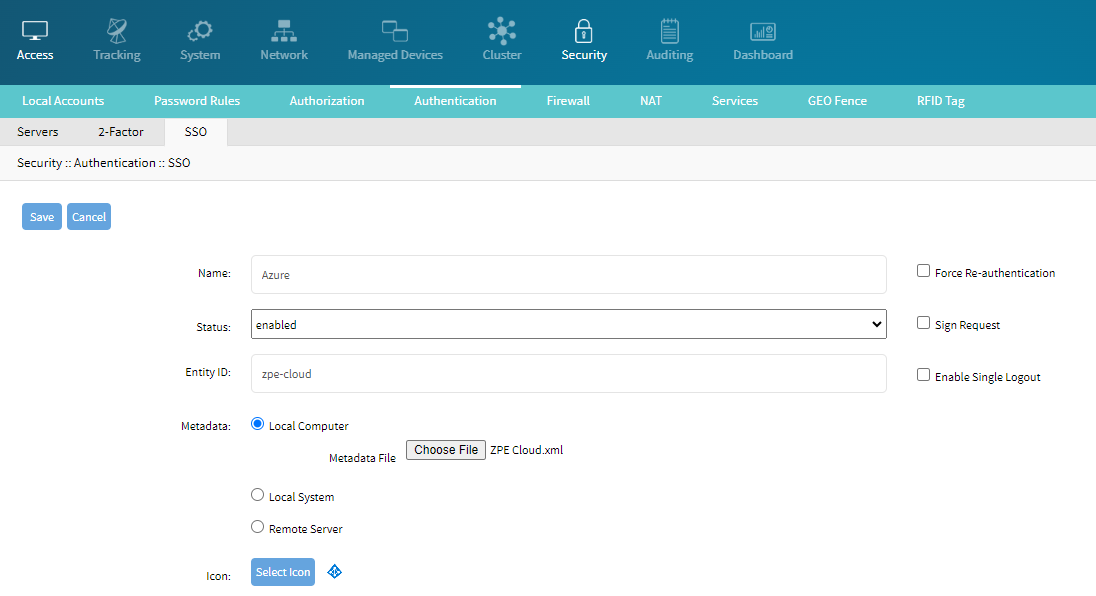
Log in to your Nodegrid device and navigate to Security :: Authentication ::SSO.
Click Import Metadata.
Add the Name.
Change the Status to Enabled
Add the Entity ID, same from Azure.
Select the Metadata file, same as downloaded previously from Azure.
Add the Icon and click Save.
Configure a local group on the Nodegrid device:
[Preferred] The name should match the one defined above in "memberOf". In this example, it is 'Administrator'.
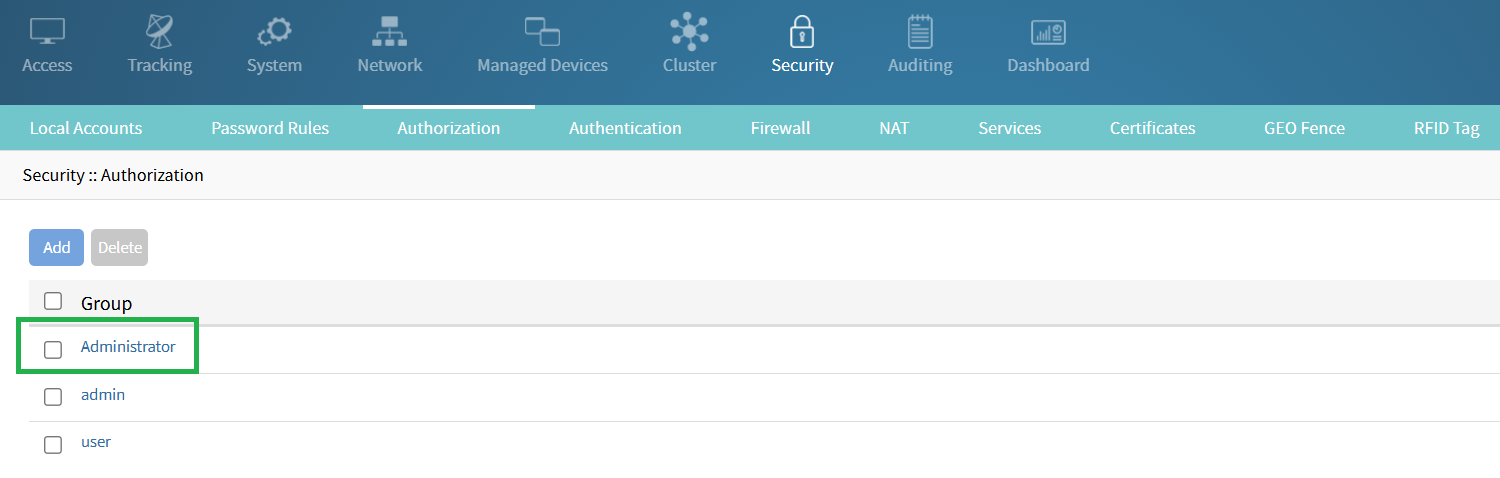
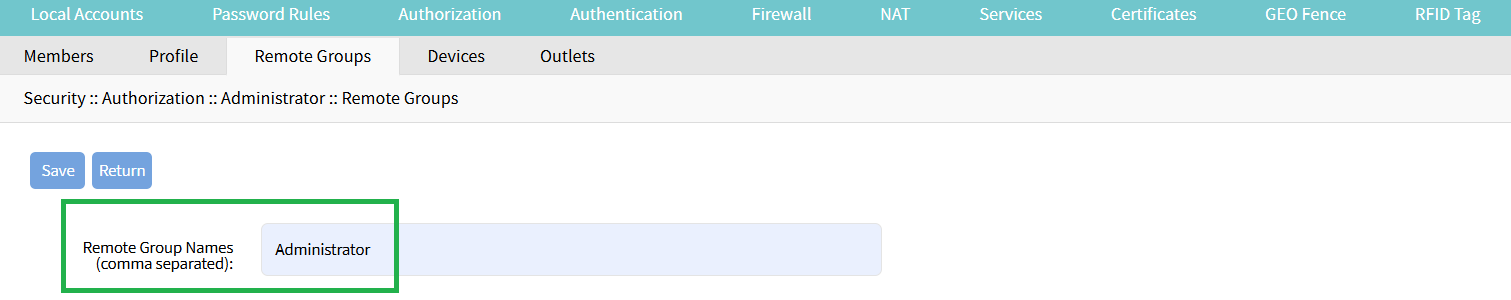
Or, alternatively, for the field "remote group" having the value defined in "memberOf". In this example, it is 'Administrator'.
NOTE
In Azure SSO URL, copy the ACS URL of the specific Nodegrid device. This enables SSO of the individual Nodegrid devices in the Azure environment.